How to build an effective threat intelligence program
Learn how building a threat intelligence program that’s effective and efficient can help you take your existing security services to the next level.
Across the world, threats are constantly evolving, and business security risks are increasing. In recent years, threats have further intensified, escalating challenges in an already overwhelming and complex security landscape. Alongside profound social instability, failure in governance and deepening polarisation between opposing political and cultural views.
We’ve seen an increase in private security organisations seeking greater situational awareness and operational efficiency as we enter the new normal, and many are looking to intelligence-led approaches as the lifeline that keeps businesses, clients and assets safe.
Why is threat intelligence important to private security?
Threat intelligence is more than simply a series of alerts.
Of course, being notified of new incidents and evolving situations is an essential part of business threat intelligence, and key to protecting the businesses, people or assets that you’re responsible for – but an effective threat intelligence program needs more than that.
Reliable, actionable and context-rich intelligence provides you with an understanding of exactly how an incident, trend or pattern is going to impact your client and their organisation, helping you better prepare for and prevent such security risks.
Unfortunately, security-related decisions are often made without this real insight or understanding. How can you effectively protect your clients if your knowledge of the threat landscape is lacking or inaccurate?
In simple terms, it’s like removing the blindfold
Matt Beer, KSS Company Director, also stated that adapting their executive protection business to have an intelligence-led approach has dramatically increased the level of proactive protection they afford their clients.
An intelligence-led approach to private security begins with understanding your client’s threat profile and the risks that may directly or indirectly target them. Once you are aware of the threats that they face, you can better direct your intelligence collection.
Our process at Intelligence Fusion includes an Intelligence Collection Plan (ICP). During the onboarding process, this session helps us to develop a deep understanding of your operations as well as who or what you’re protecting.
Because we’ve built a fully operational 24/7 intelligence unit, we can quickly adapt and respond to the growing needs of you and your clients.
For example, if you’ve recently won a new contract, or perhaps you’re currently working on some proposals in order to win new business, you may need us to start collecting intelligence in new areas that weren’t part of your original collection plan. These requests may be temporary or long-term – either way, we’re structured in a way that allows us to quickly and easily react to changing requirements and new business threats.
Do I need to build a threat intelligence program?
Are you responsible for the safety and protection of people or assets?
Whether you’re providing executive protection, risk consultancy, travel risk management or emergency response, having access to a continuous stream of data will vastly improve your understanding of the threat landscape.
Being more informed and having immediate access to the latest intelligence will ultimately enable you to better advise your clients, regardless of their requirements.
Do you have an international footprint?
If you have clients traveling across the globe, you’ll need a constant awareness of what’s happening in those places. Building a threat intelligence program can give you exactly that.
The needs of travel security companies are complex – in addition to the physical threats your clients might face, there’s a need to understand the geopolitics of each region, as well as any government changes or developments that may affect movement or the way your business can operate within the country.
Do you work in a saturated market?
If you operate in a competitive space, a threat intelligence unit can take your services to the next level and give you the edge you need to acquire and retain your client base.
You can provide elevated situational awareness perfect for pre-travel, route and risk assessments, country or regional reports, as well as being useful for live-monitoring of a place or area during travel or client movement, too.
Having a database of intelligence can also help you to justify your services by highlighting the various risks to your client and demonstrating the potential of threats to escalate.
Answering yes to any of the above questions means that your business operations would benefit from the development of a threat intelligence unit, whether internal or outsourced.
How to build an effective threat intelligence program
A well-built threat intelligence program will provide a useful and precise insight into the global security landscape – helping you to:
- Understand past and current threats as well as help forecast future ones
- Contextualise potential threats
- Quickly triage and process incoming information
- Prioritise and allocate your resources more efficiently
- Improve your team’s performance
- Save time, money, and in some cases, lives
So how to go about building a threat intelligence program – and what do you need to make sure it’s effective?
1. Creating an intelligence team
Highly-trained intelligence analysts with appropriate technologies and collection methods are critical to a successful threat intelligence program.
A conscious effort should be made to build a team of threat intelligence analysts with diverse skills and analytical expertise. Analysts may be specialists in a variety of domains due to past experience, their education or even their location and having a good blend of interests and capabilities is recommended.
Our analyst team at Intelligence Fusion is not only made up of a wide-range of backgrounds, careers and experiences but every intelligence analyst is a graduate of our military-standard intelligence training program, ensuring consistency and maintaining high standards across our collection and reporting.
The intelligence training consists of a diverse range of modules, all built using real-life experiences, case studies and examples from our intelligence teams’ previous careers spanning multiple countries and sectors. These useful hooks of knowledge and tangible scenarios help trainees to absorb and retain information.
Ideally, training should be provided to everyone working within your threat intelligence unit, including senior management in order to ensure clear standards and cognizance across the department.
2. Setting standards
Written procedures are also key to maintaining quality within your threat intelligence program. Your analyst team should follow a defined methodology of direction, collection, processing and evaluation and dissemination – also known as the Intelligence Cycle.
Due to the vast amount of data available, the intelligence cycle provides an order to the collection and information gathering process. It states exactly what needs to be collected, in what priority and when.
Timely, accurate and actionable intelligence requires a formal yet flexible process based on sound principles. The Intelligence Cycle is a tried and tested methodology used for planning and decision-making across different military forces around the world.
With a history of working in military intelligence here at IF, the implementation of the Intelligence Cycle and other military doctrine provides structure, consistency and ensures high-standards across our team. Most importantly, however, it helps us focus our collection efforts to best meet the needs of our clients and the people they protect.
3. Building your source list
Intelligence Collection is the most time consuming element of the cycle, especially if you have multiple clients with multiple requirements.
Our clients providing security consultancy have previously spent days gathering enough historical data to make sure their assessments and reports were as comprehensive as possible – a time consuming and resource intensive task that meant client briefs couldn’t be planned and conducted at speed.
Creating a source list that you can rely on to provide accurate and up-to-date information will save you time, money and allow for a much shorter turnaround time when it comes to clients’ requests and last-minute travel arrangements.
The team at Intelligence Fusion has spent years building and refining an extensive source list of over 12,500 individual references that we use to quickly identify information, before analysing and disseminating to clients.
And because we have a broad spectrum of skills and expertise within our 24/7 Operations Centre, we’re able to meet the needs of clients across multiple industries too.
4. Managing your data
From understanding the historical landscape of a region to precisely geolocating incidents, building a library of reliable open source tools and technologies will help your threat intelligence team cut through the online chaos and manage your data collection efforts efficiently.
As your source list grows and your database of incidents expands, being able to quickly access historical intelligence will also save time during future assignments. Knowing you can tap into your entire back catalogue of data will also ensure that there’s never any duplication of effort from your team, re-collecting data that’s already available in your archives.
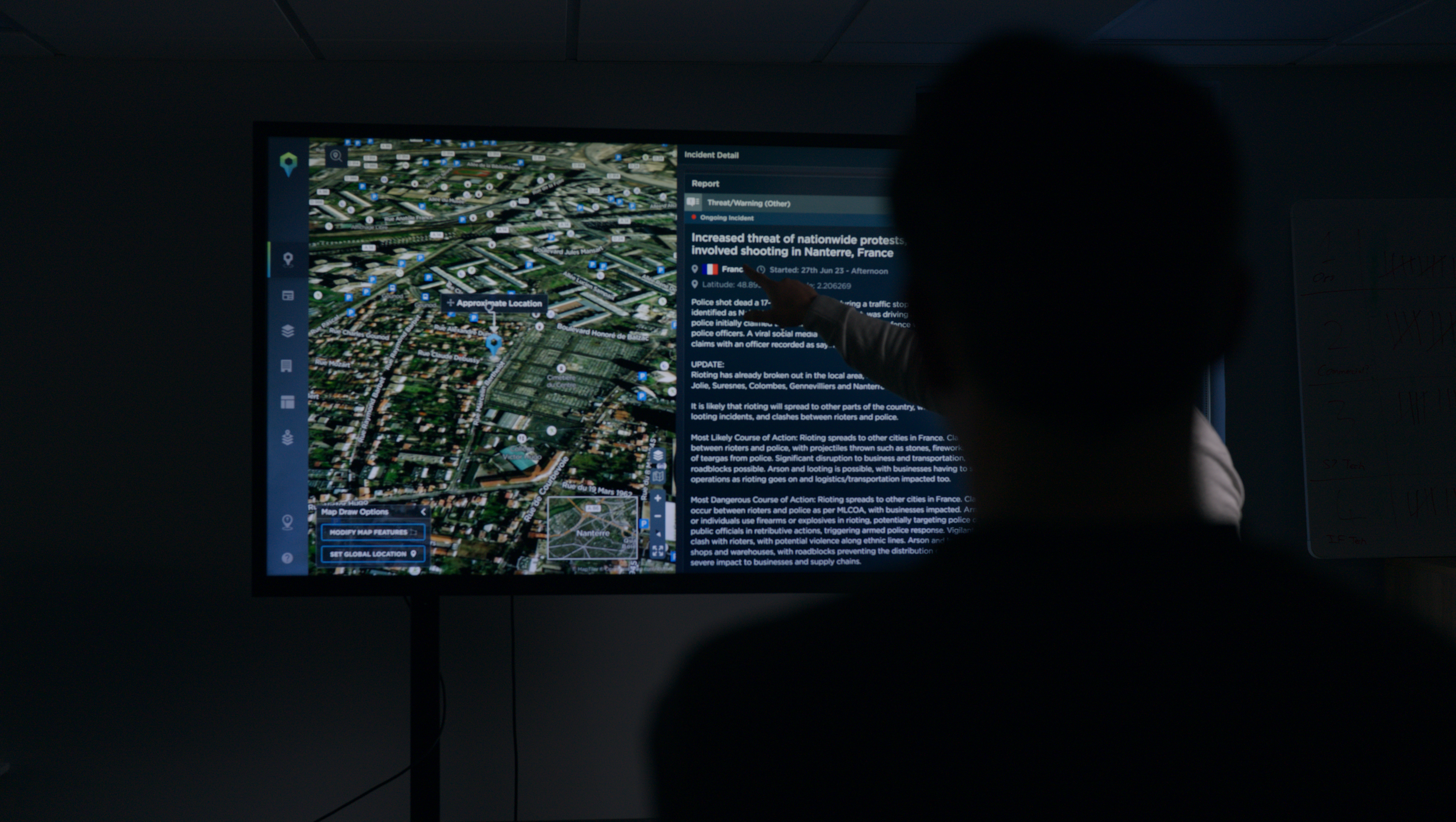
It’s also important that intelligence is visualised in a way that provides clarity and context, helping you to understand what’s really happening and why it matters to your client.
This is why we emphasize the way incident data looks within our threat intelligence platform. We’ve designed and developed an award-winning user interface with powerful visualisation tools that are vital to helping our clients digest information at speed.
There are also extensive filtering options that allow users to deep-dive into over 1,200,000 incidents worldwide. So, researching and understanding new environments has never been easier.
There’s a lot to consider when it comes to building a threat intelligence program, and there’s no cheap or easy way to do so. A reliable intelligence capability requires a significant investment of time, resources and money but it can also be fundamental to providing a next-level service.
Providing a more valuable service to your clients doesn’t always mean that you have to build an internal outfit, however.
Intelligence Fusion can provide a number of services and solutions to help you become intelligence-led. From technology to training and even hiring your team, we have multiple ways to make the process more cost-effective and efficient.
If you’d like to learn more about being an intelligence-led security company and how we can help, speak to a member of our team today.