Unifying Security and Risk in the Manufacturing Industry
Manufacturing is a complex industry that relies on strong relationships with various countries. Supply chains can span vast areas, cross multiple borders, and encroach on numerous territories, hence facing many threats. Businesses operating in this industry must be vigilant and agile. Having knowledge of the physical and corporate threat landscape and being able to effectively manage risk is essential. Fast, accurate data with added context allows security professionals to work with risk leaders to successfully protect their people, assets and businesses.
Our data highlights some of the most prominent examples of threats within the manufacturing industry. In this blog, we review the impact of these threats on manufacturing and how businesses could prepare for change in the market and reduce their overall risk level, mitigating problems before they occur.
The high-value nature of goods as they transit through supply chains makes them tempting targets for criminal groups. Naturally, this can impact an organization’s profits but also its reputation and, in extreme cases, can pose a security threat to employees. Security threats can also be fueled by a dislike of a brand and the values it stands for or other extreme views, which can cause negative consequences.
An example of a negative situation occurring as a result of actions undertaken by a manufacturing company materialized in June 2023.
Approximately 200 people protested in front of Teflon chemical manufacturing company Chemours at Baanhoekweg, Dordrecht, Netherlands. Protesters were demanding the closure of the company due to groundwater pollution.
A TV show that aired on local networks revealed health concerns and damaging contamination caused by the Teflon manufacturer – formerly controlled by U.S. company DuPont. The show alleged that they had concealed this information for years, knowing that the groundwater around the factory and landfills in Dordrecht were heavily contaminated with a PFAS variant (PFOA).
These demonstrations occurred on a weekly basis; activists were demanding that Chemours reduce PFAS emissions to zero. The reputational damage caused by the awareness raised from this protest activity could have a hugely damaging impact on Chemours.
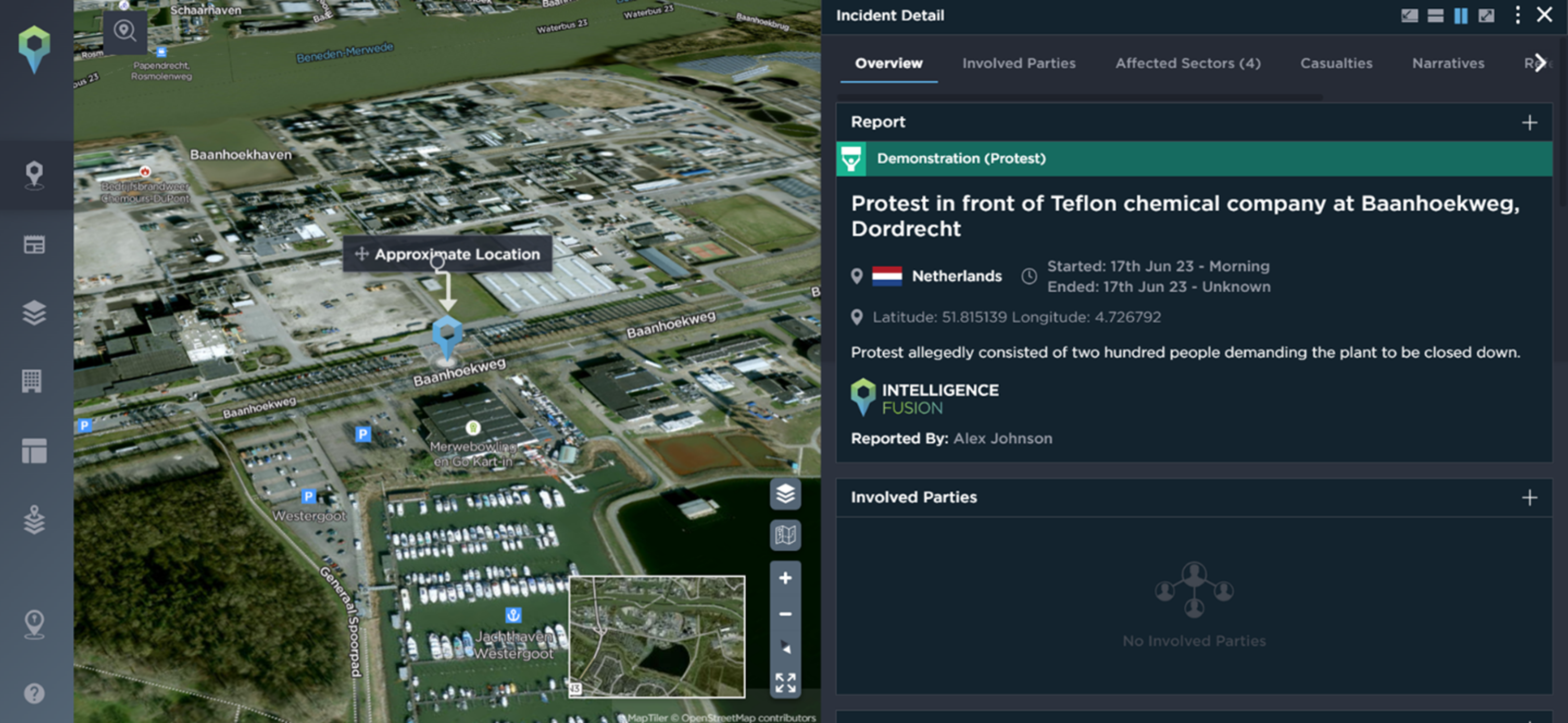
An example of one of the protests at Chemours [Image source: Intelligence Fusion]
Threats can also emerge when companies do not do their due diligence before setting up an operation in a new area or do not show respect for local communities and protected areas.
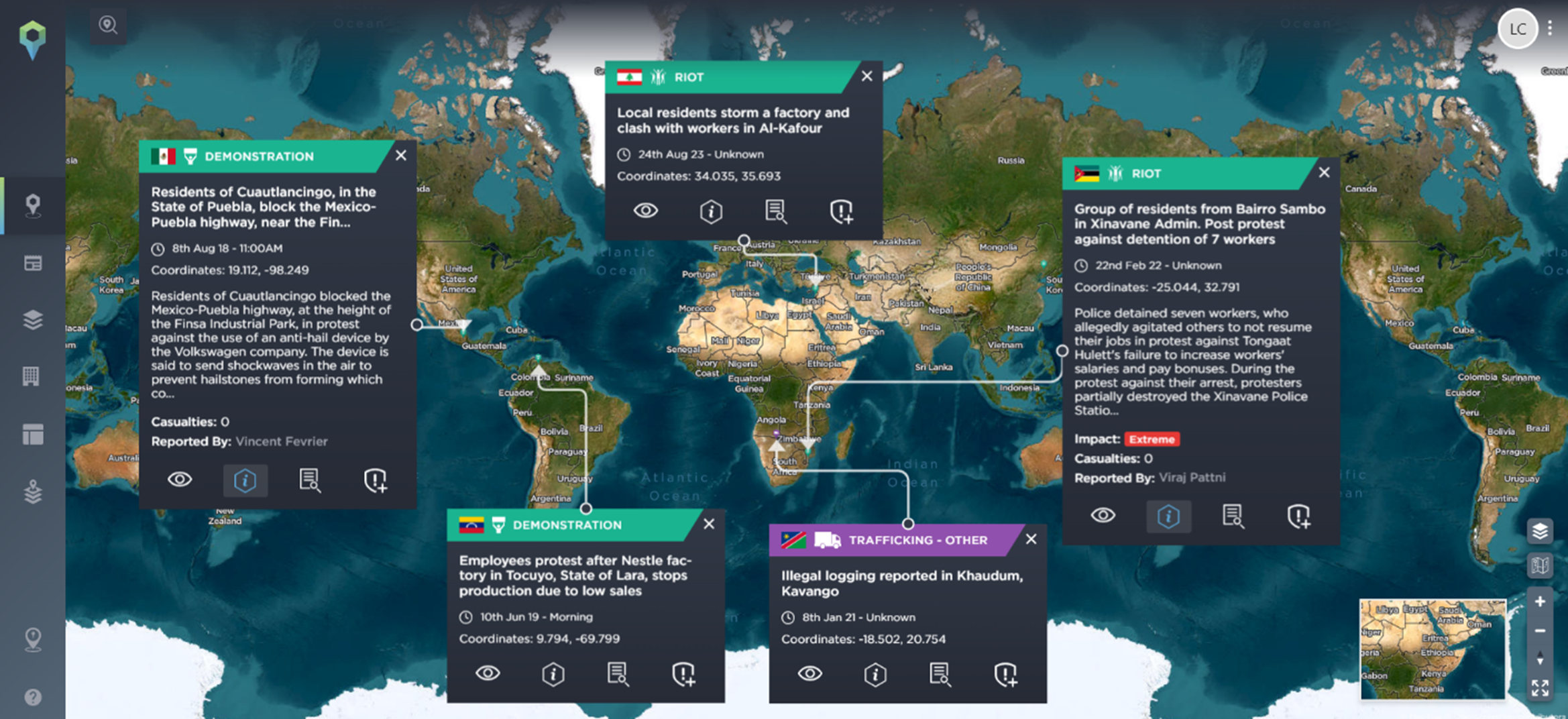
Incidents of manufacturing companies impacting local communities [Image source: Intelligence Fusion]
Supply chain disruption
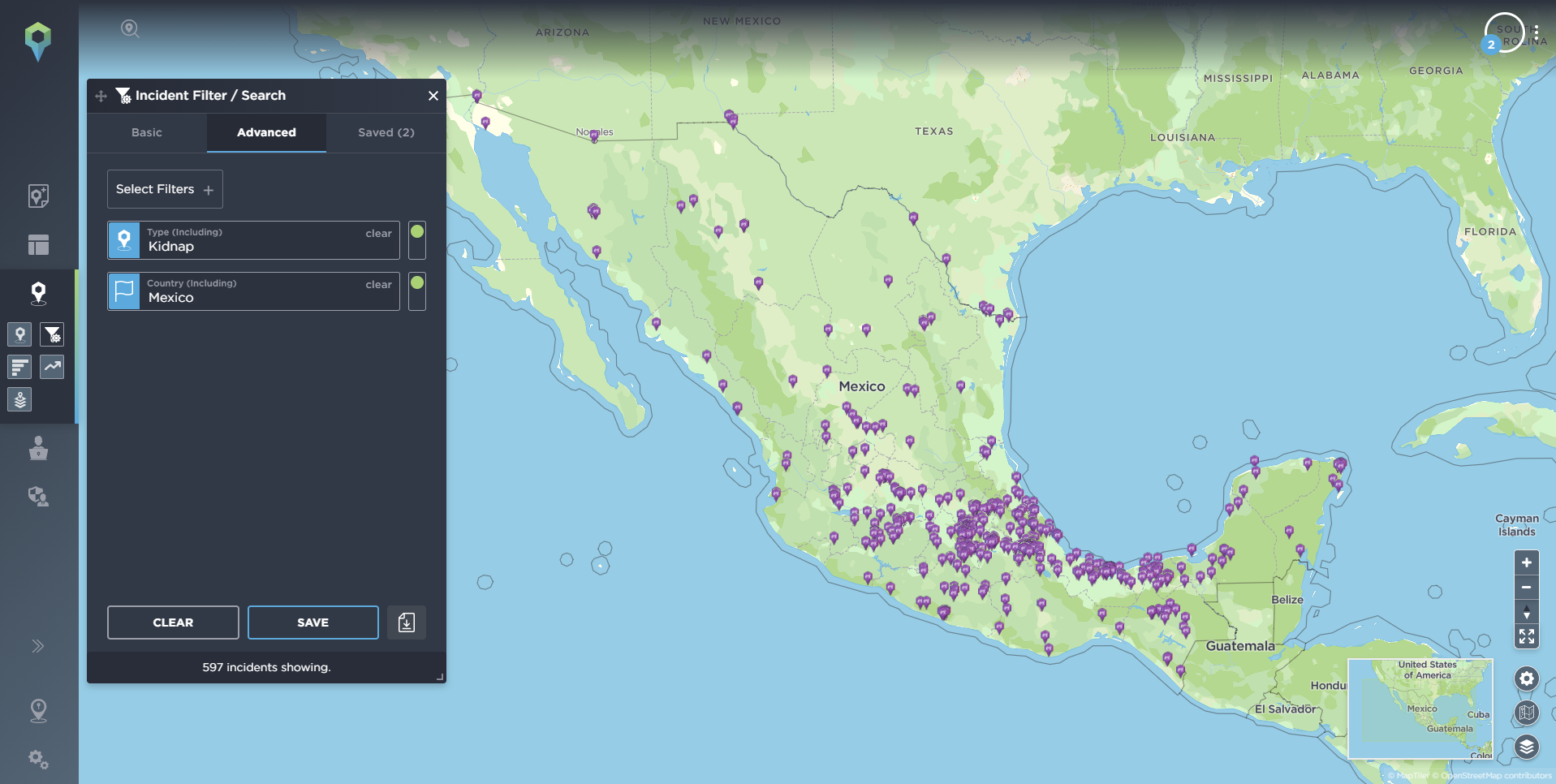
Our data shows that supply chain disruptions are the most common and widespread threat to the manufacturing industry. As part of Sigma7, we support our clients with supply chain risk management and crisis management plans, and when onboarding with Intelligence Fusion, we use an Intelligence Collection Plan (ICP) to ensure we understand your goals and priorities in detail.
Supply chain threats are often out of your control; they can occur at various points and can range from natural disasters to theft or cyber breaches. Where possible, we aim to alert you ahead of an incident occurring if the information is available, e.g., for a planned protest or strike. Hence, when mapping supply chains, entering a new market or expanding operations, due diligence is required to understand the landscape and the unique country, regional and city risk to your business on a local level. In addition, continued monitoring of threats and risks in the market can protect you against emerging issues and provide cyber resiliency.
Some incidents can be quite insignificant and siloed, whereas others can be far-reaching and have major consequences for multiple businesses and sectors. Having accurate, up-to-date threat intelligence allows manufacturing businesses to understand the risk level in the chain, map out vulnerabilities, conduct stress tests and put disaster prevention strategies in place. However, there will always be situations that are unexpected; in these cases, security and risk professionals need to understand as much information as quickly as possible to successfully protect their people and assets whilst limiting the impact on business operations.
An example of a major incident that impacted supply chains globally was in 2021 when the Suez Canal was blocked for six days by a container ship. On 28th March, at least 369 ships were queuing to pass through the canal, stranding an estimated US$9.6 billion worth of trade.
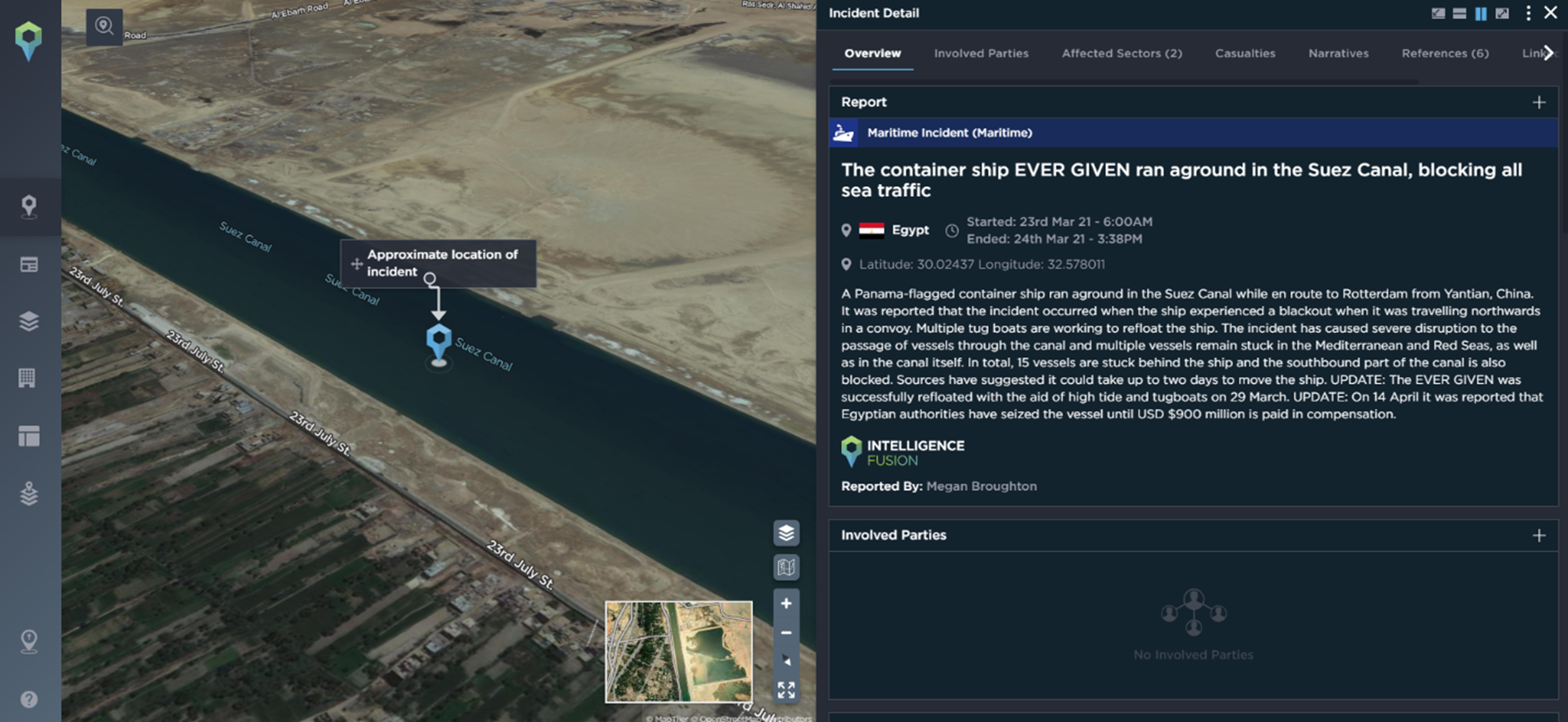
The Suez Canal incident, mapped on the Intelligence Fusion platform [Image source: Intelligence Fusion]
The impact of this blockage was far-reaching for businesses across multiple industries. Being alerted to this kind of disruption in a timely manner is essential for operations to run smoothly. It allows ships to dock elsewhere and businesses to forge new, temporary supply chains or be reactive and increase their delivery cost to customers who want their items fast, meaning they transport them via air instead. As our team of intelligence analysts verify and assess every incident before mapping it, subscribers to our platform can be confident in their decision-making ability and quickly select the route that suits their needs best. Alerts on the Intelligence Fusion platform also ensure that security teams are quickly informed of the incident initially, but also any further updates our analysts may add to provide further context and insight.
Insider threats
A less common threat to manufacturing companies is insider threats. However, intellectual property theft, including unauthorized access or theft of trade secrets, in person or via a cyber-attack, can lead to a loss of competitive advantage and counterfeit products in the market can cause damage to a company’s reputation. Being alerted as soon as espionage or theft has occurred within the market can provide a competitive advantage and guidance regarding areas of weakness that your business should strengthen. In addition, understanding geopolitical context allows security teams to better apprehend the factors driving espionage and the tactics used. This information can also be fed to the risk management team for consideration in future analysis work.
An example of espionage occurring within a manufacturing company happened last year in Albania. Two Russians and one Ukrainian were arrested after a suspected spying raid on an Albanian arms factory. One of the male suspects allegedly attacked the guards with a paralyzing spray while trying to take photographs of the Gramsh factory, which is used for dismantling derelict weapons. During communism, the Albanian Gramsh plant was used to produce the Russian type of rifle AK-47.
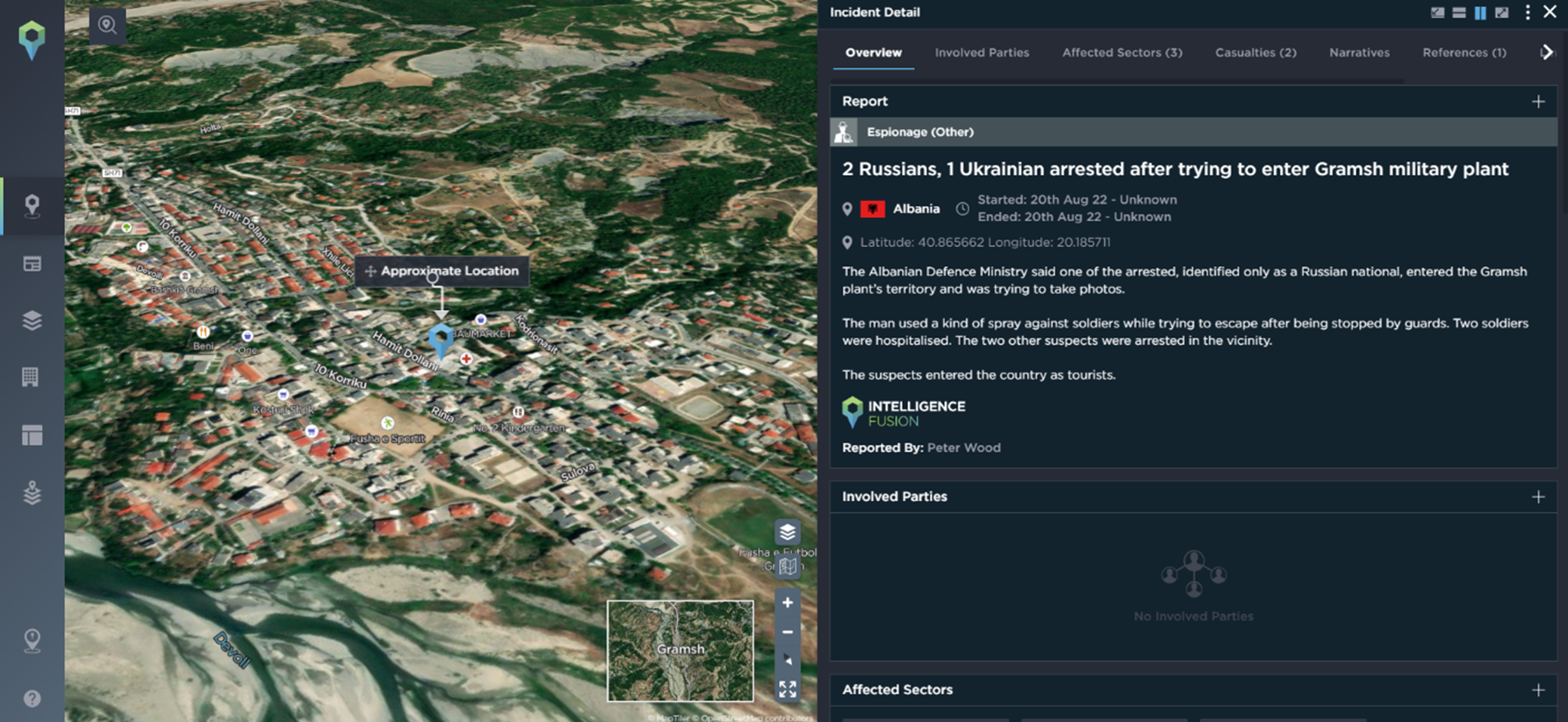
An example of espionage affecting the Manufacturing industry [Image source: Intelligence Fusion]
Product safety
Macro factors can have an unexpected impact on your organization; external threats can cause internal pressure, which can impact product quality and safety. In addition, due to the complex nature of some supply chains, shipments can be vulnerable to infiltration and become compromised; hence, extreme due diligence is required to ensure product safety is upheld.
Illegal activity surrounding counterfeit products can be frustrating and cause brand damage, but it can also be extremely dangerous, even causing death if users purchase a product, not realizing it does not have the same safety standards as a legitimate product. This kind of threat can, therefore, range from insignificant to extreme. Threat intelligence regarding what is occurring within the wider industry and supply chain, as well as which actors operate in different regions, can make organizations aware of specific routes and gangs they should monitor to increase security precautions.
Incidents of counterfeiting are common, with a noteworthy example occurring in 2020, when 15,000 bottles of illegal alcohol were seized in Semenovskoye, Moscow, in Russia.
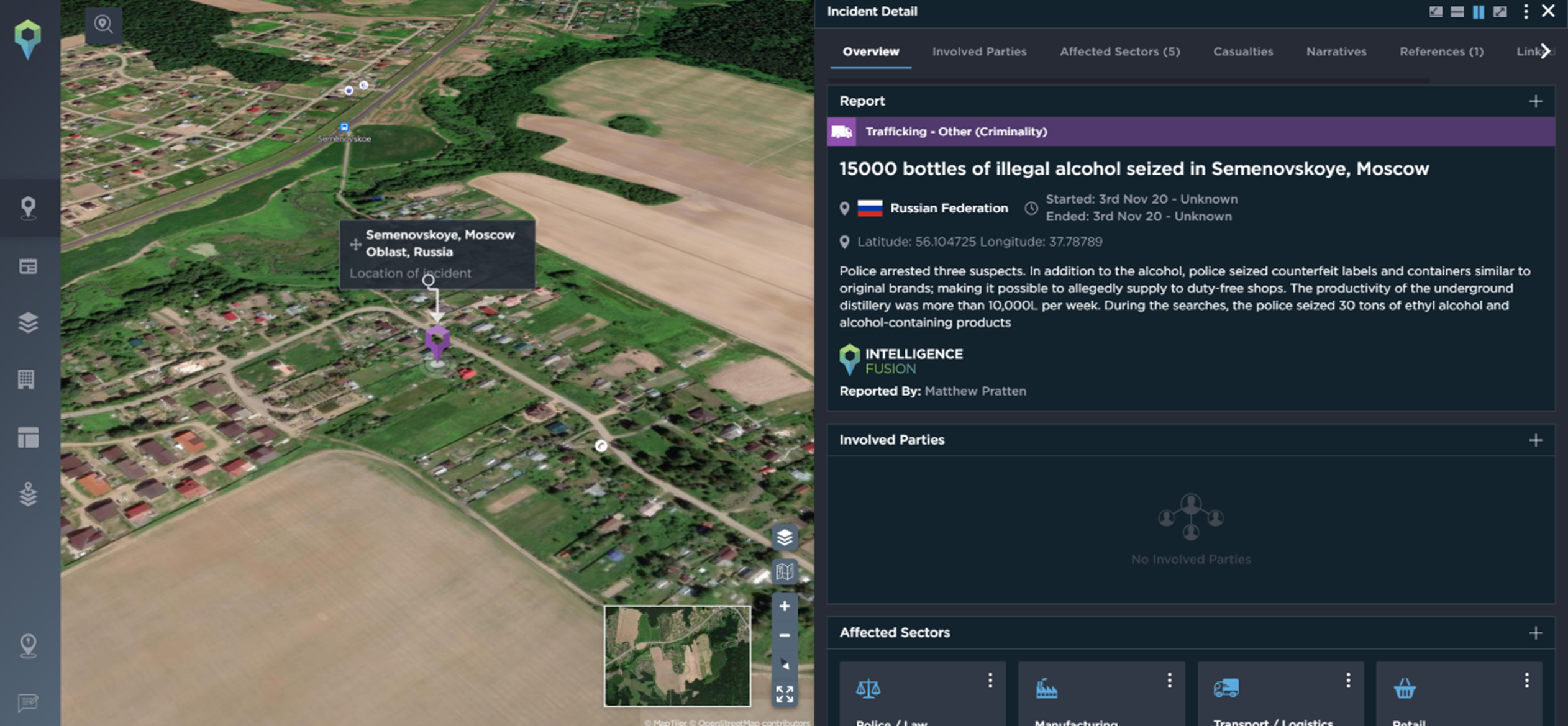
Counterfeit bottles of alcohol seized in Russia [Image source: Intelligence Fusion]
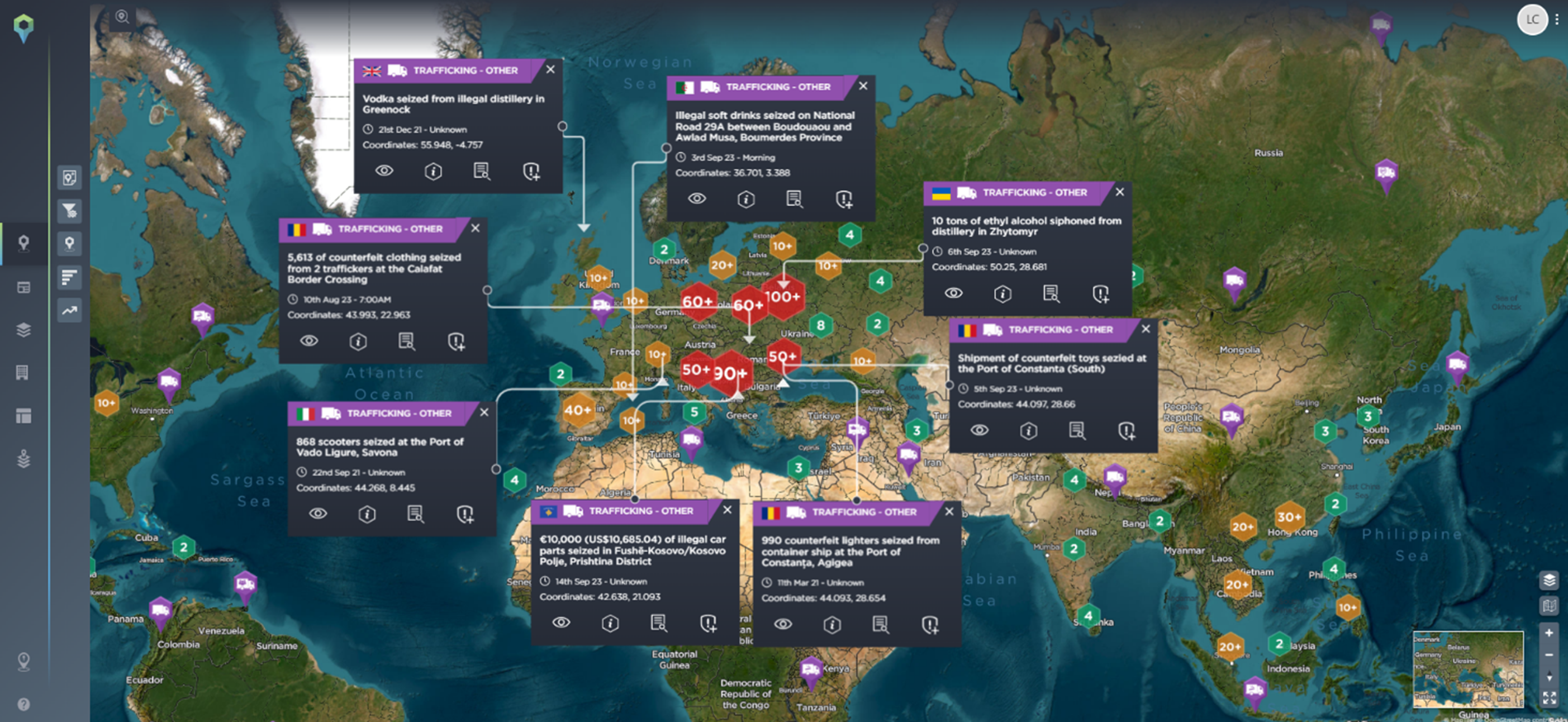
Trafficking incidents affecting the manufacturing industry. The most prominent area for this type of activity is Europe [Image source: Intelligence Fusion]
Employee welfare
Major disease or extreme weather conditions can impact workers’ welfare, which can, in turn, impact business operations, productivity and deadlines. But, employees are also vulnerable to criminality in and around your static assets; therefore, if you operate in a high-risk area, this may prompt the implementation of further internal security measures.
An extreme example occurred in May 2023 when two male employees were shot and killed in a Mercedes-Benz plant in Sindelfingen, Germany. Security staff detained the perpetrator and handed him to officers, who arrested him without resistance. The motive behind the shootings is unknown.
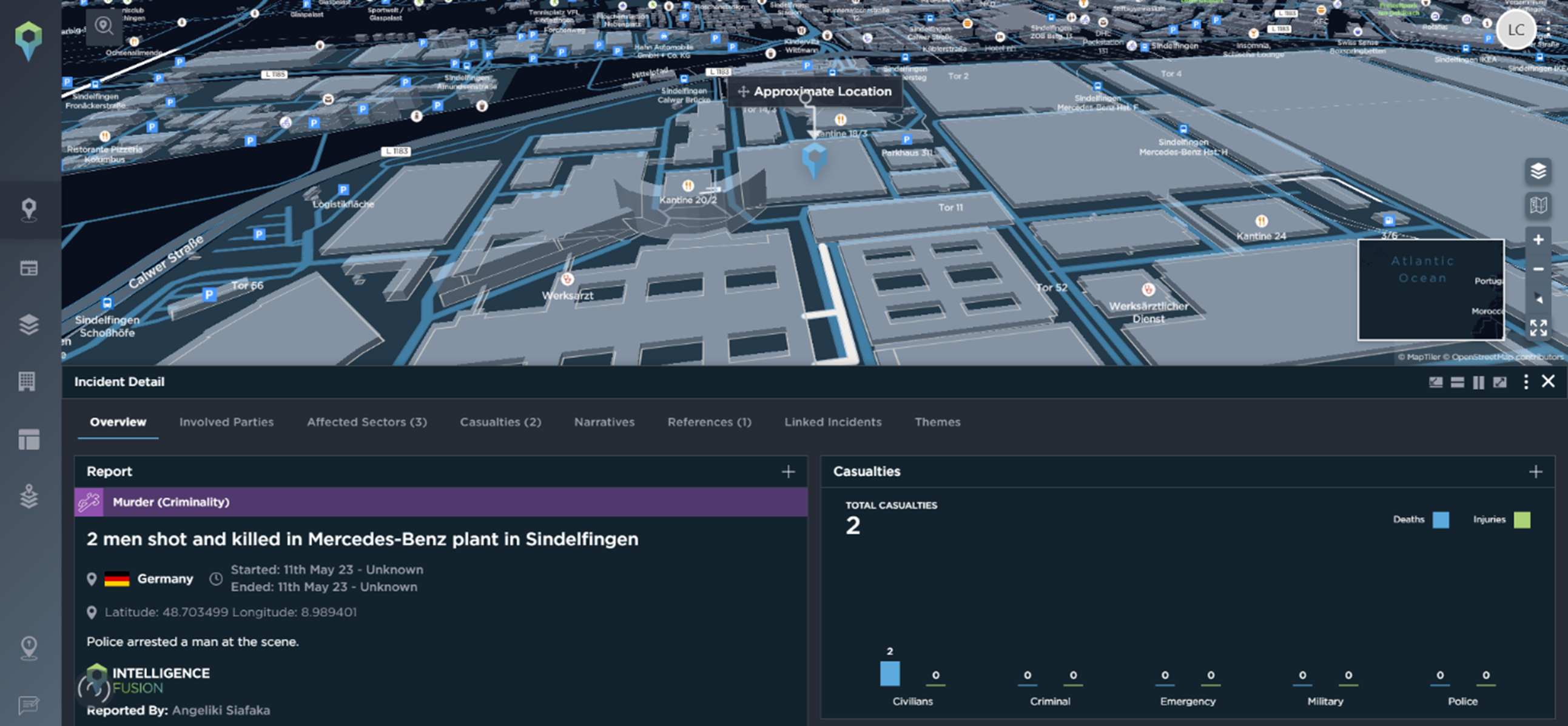
An example of a physical security incident impacting employees [Image source: Intelligence Fusion]
However, employees travelling for work can be in the most vulnerable position. Being able to conduct risk assessments for countries frequently visited by your employees and save them in a central location on the platform for all users to access streamlines processes and makes sure everyone is kept informed should a situation change. Taking this unified approach to risk benefits the security managers as they can have more of a proactive outlook, mitigating issues before they occur. In addition, real-time updates on our news feed allow subscribers to quickly filter thousands of articles within minutes of them being published to stay up to date with the latest developments. The threat map also provides a high-level overview of the safety of a country, allowing businesses to categorise how they view threats. In addition, bespoke assessments can be conducted by Sigma7 for more in-depth analysis, if required.
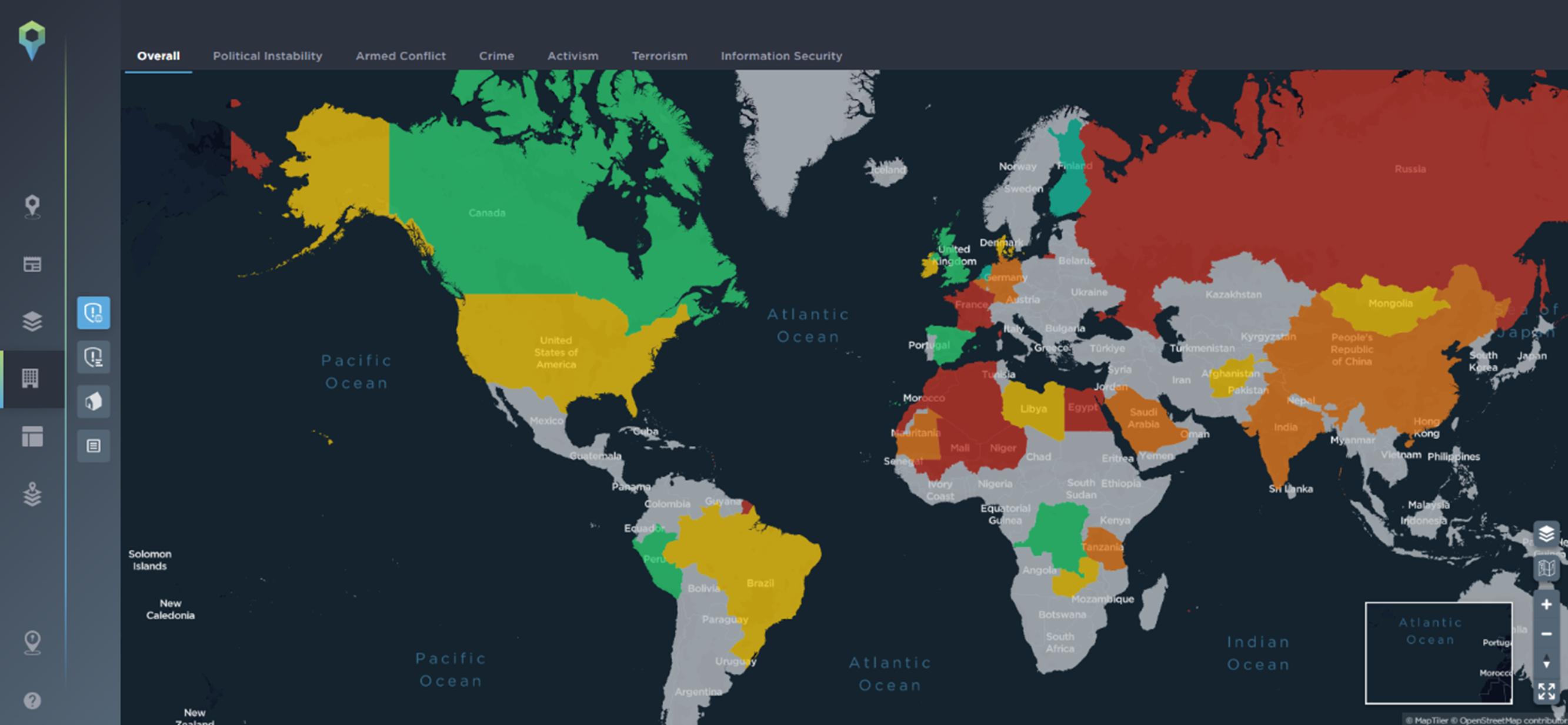
The threat map is a premium feature of the Intelligence Fusion platform allowing subscribers to categorise and visualize threats in terms of political instability, armed conflict, crime, activism, terrorism, information security or other areas depending on what matters most to your business. This can be fully customized to provide the maximum benefit [Image source: Intelligence Fusion]
Asset protection
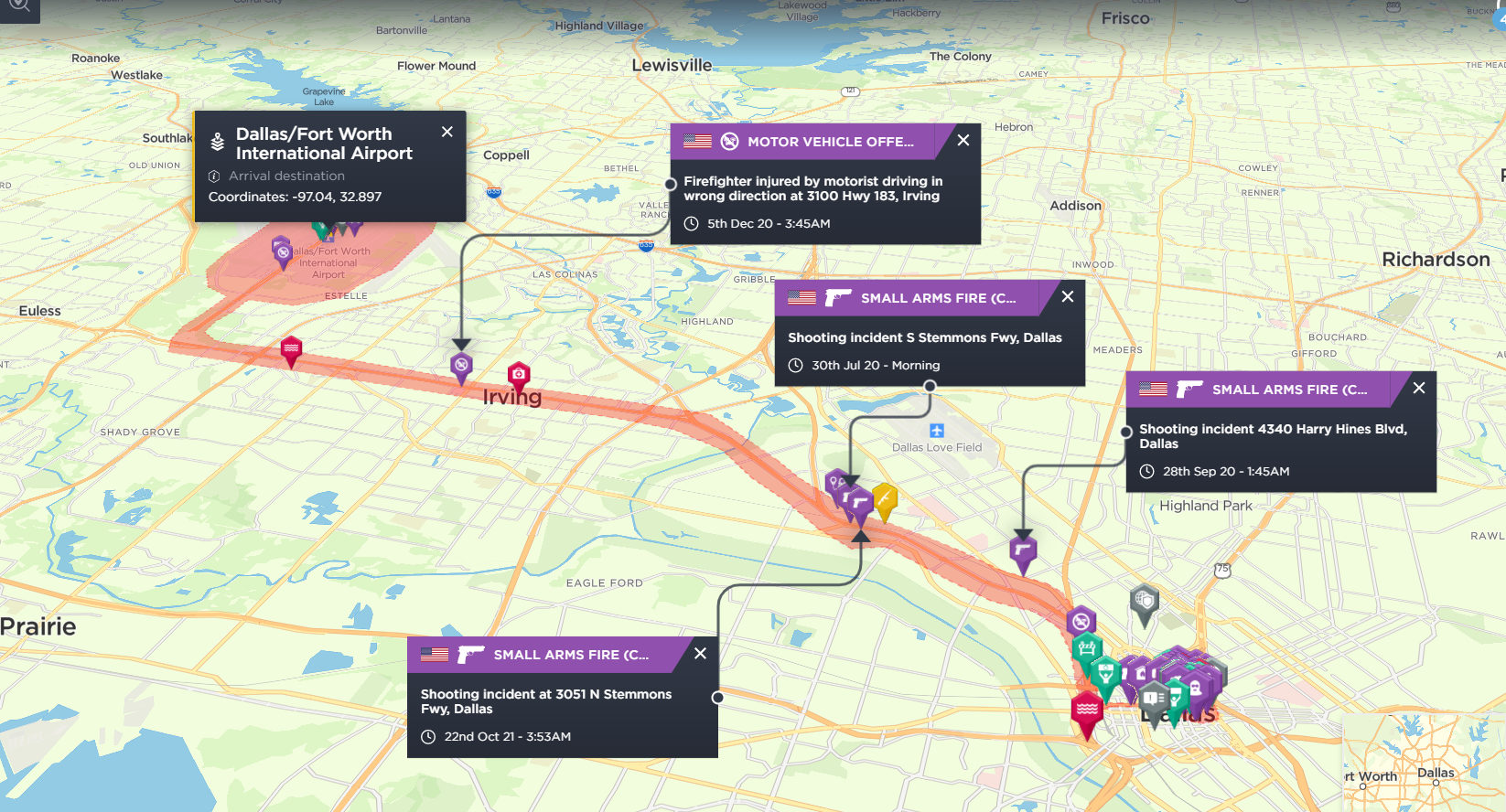
As a subscriber, your static assets are mapped onto the platform, and alerts can be set up within a radius of the area to alert you and your team as soon as an incident occurs that could have an impact on your business. For example, if you had a factory in Georgetown, Kentucky, being made aware of severe weather alerts and criminality near your factory can be an important element of protecting it, e.g., through flood prevention measures or informing staff not to leave the premises as there has been a fatal shooting nearby.
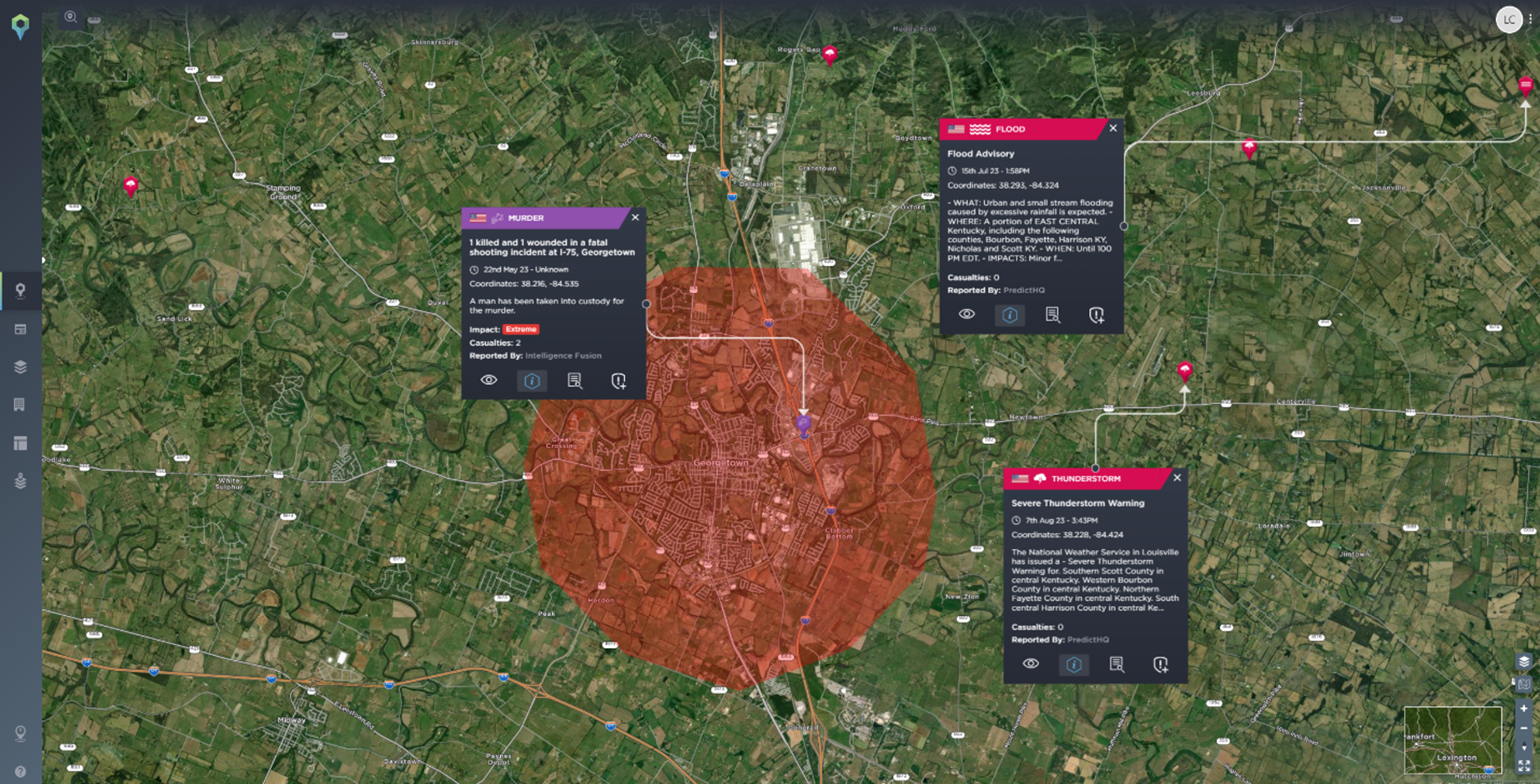
Geofencing can be used when filtering your search to view incidents within a certain area; this can be useful for a quick assessment of a tailored area [Image source: Intelligence Fusion]
In addition, knowing the vulnerabilities within your assets, e.g., areas that are more liable to flooding, can allow you to invest wisely in preventative maintenance. Risk engineering solutions allow risk managers to review exposure values to calculate the potential loss value, strengthening your internal risk profile and further protecting your operations. As a security manager, this data-driven approach prevents threats from occurring and future-proofs your assets, making it easier to protect your employees.
Therefore, if you are a manufacturing company, we can offer an integrated approach to risk which is unique to your business needs. Whether you’re concerned about corruption, sanctions or the day-to-day threats to your business, we can support your needs. So far this year, the top categories impacting the manufacturing industry are fire, demonstrations, trafficking, explosions and industrial incidents, and the continent’s most heavily impacted are Asia and Europe.
Discover more about risk mitigation; schedule some time to speak to a member of our team.