How to set up a mining operation using threat intelligence
Learn how accurate threat intelligence is key to setting up a mining operation - and mitigating any continuing mining security risks faced throughout the lifetime of its operation.
The actors who form the mining sector are diverse, ranging from multinational companies who are highly regulated, through to small scale criminal enterprises who use child labour in places like the Democratic Republic of Congo. There are also questions around the ethics of mining, which are becoming more prominent as the global environmental movement grows, along with public consciousness regarding human rights and the role of the private sector. As such, there are a number of mining industry risks that need to be considered when setting up a mining operation.
Issues linked to the mining sector are normally in relation to:
- The environmental impact of mining e.g. impact on water supply, hazardous material use, air and noise pollution.
- Labour risks e.g. health and safety, male dominated industry with women facing discrimination.
- Economic and social disruption due to influx of outside workers, which can strain local services and increase prices due to higher incomes, as well as the potential to change social dynamics by increasing inequality.
- Security incidents often linked to the mining sector’s use of private security or government forces.
- Land acquisition e.g. unfair or insufficiently negotiated land acquisition, displacement of communities, changes in land use and impact on traditional economies.
- Treatment of indigenous people e.g. social exclusion and large scale expropriation of land and resources.
- Bribery and corruption, especially in autocratic countries, often linked to state owned enterprises and politicians.
Because of the above, threat intelligence is absolutely key to the mining sector. In this report we’ll explain how threat intelligence can be used to set up a mining operation, but also how using threat intelligence can support and protect ongoing mining operations.
The process of operating a mine consists of:
- Prospecting and Exploration
- Mine Design and Planning
- Production
- Closure and Reclamation
Taking these step by step, let’s explain how threat intelligence can help.
Prospecting and Exploration for Mining
During this first step of setting up a mining operation, typically smaller companies, known as juniors, identify areas where ore can be found and take core samples to evaluate grade and weight of deposits. Once the value of the deposit has been determined, a feasibility study is then conducted.
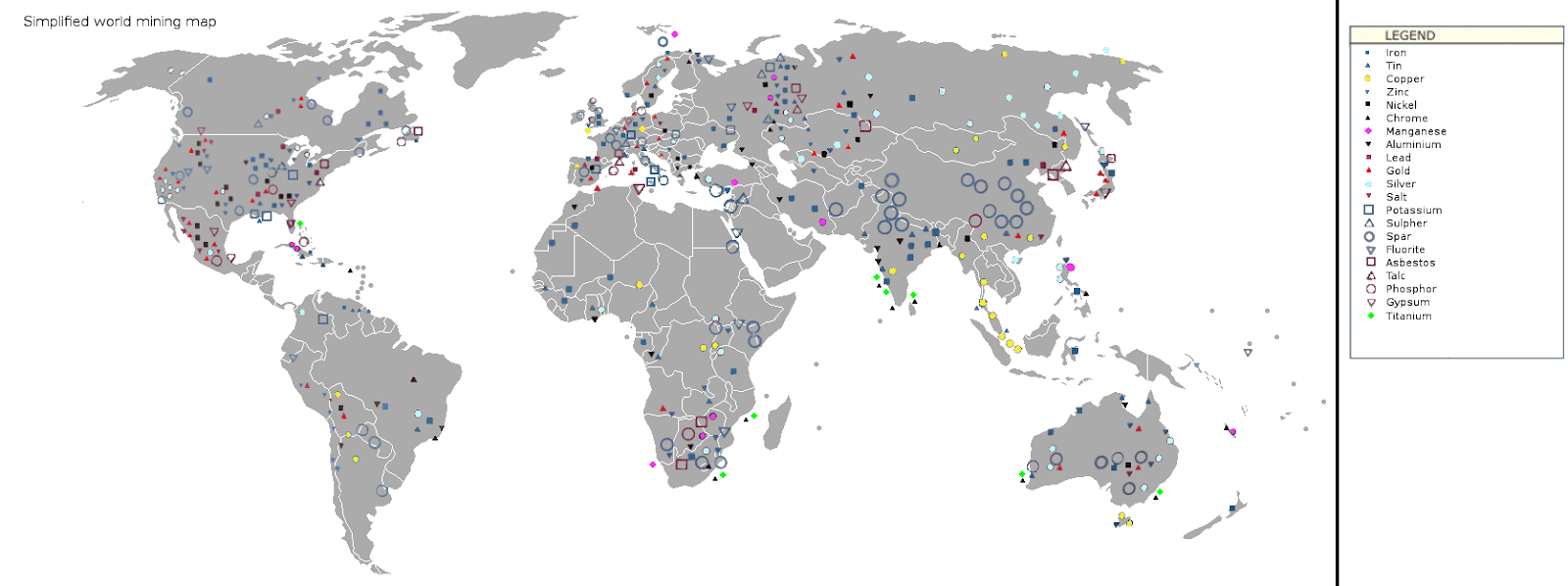
Simplified World Mining Map.
Source: https://upload.wikimedia.org/wikipedia/commons/8/82/Simplified_world_mining_map_1.png
As the above map shows, ore is located across the world and therefore the threat profile of these mining locations varies not just between countries, but also the regions of a country.
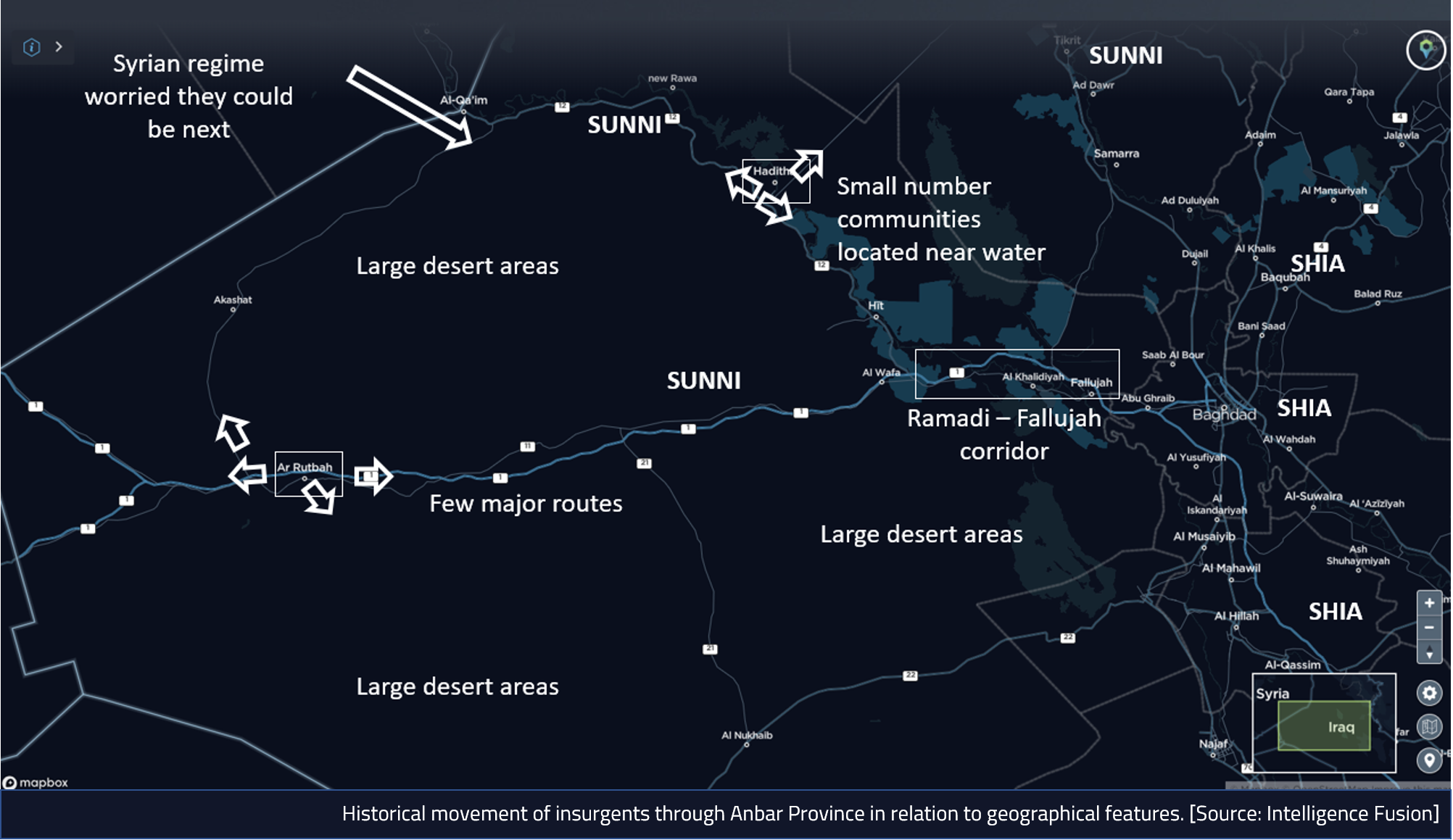
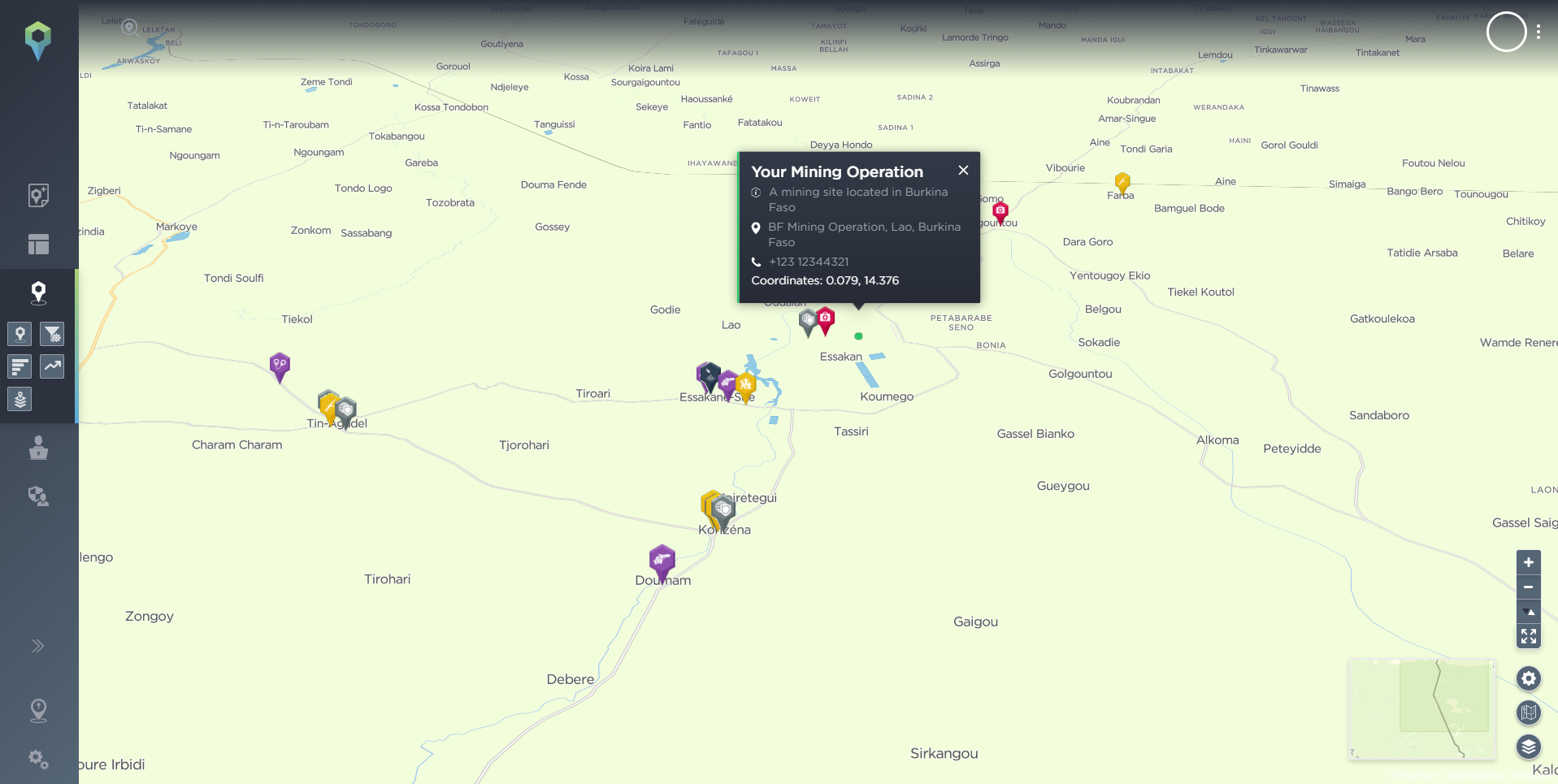
As an example, let’s say a mining organisation wants to operate the Akashat Phosphate Mine in western Iraq.
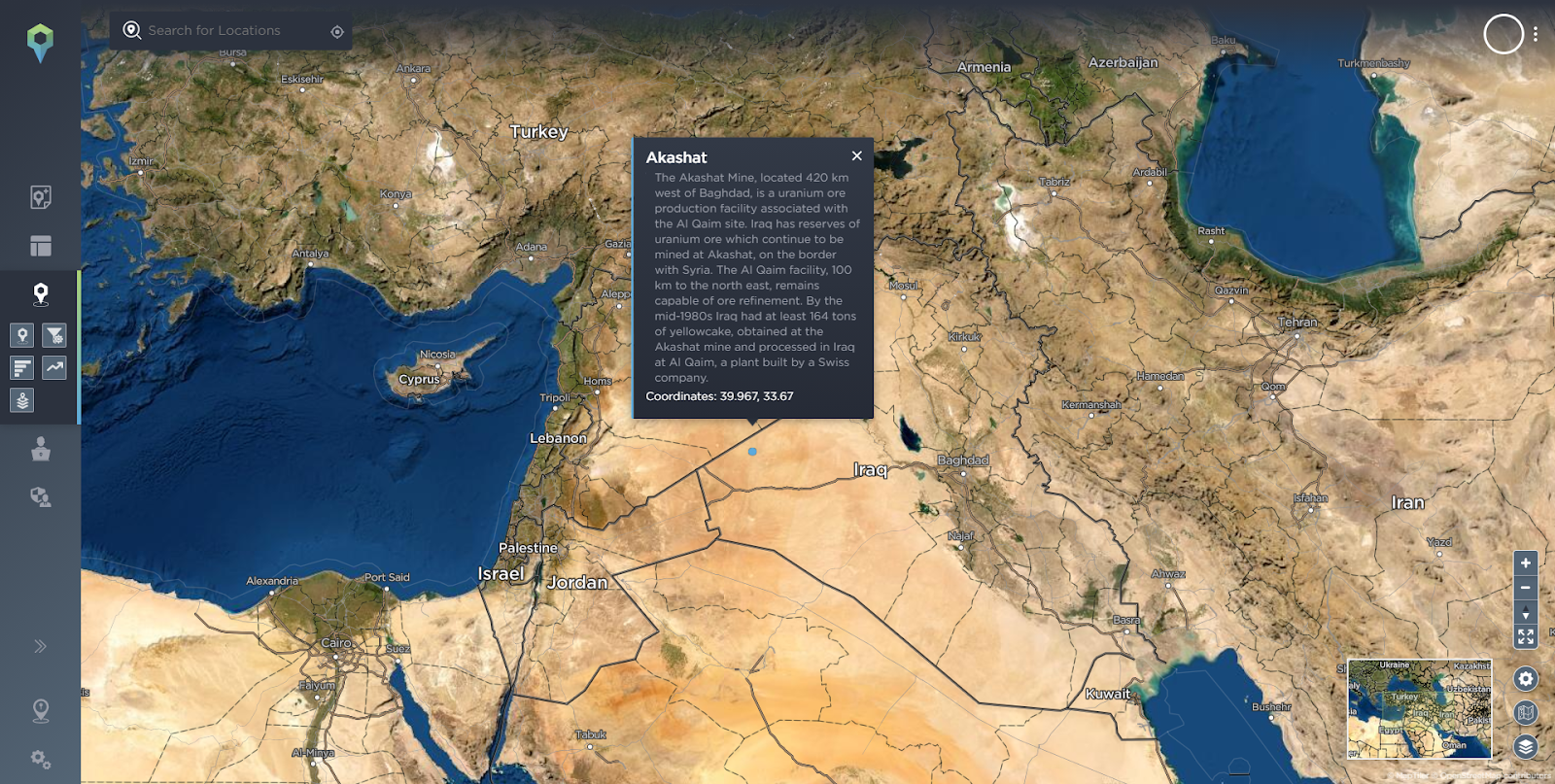
Location of the Akashat Phosphate Mine.
Source: Intelligence Fusion.
Before prospecting or exploration is even attempted, a review of the Intelligence Fusion threat intelligence platform allows us to look at the threat at the tactical, operational and strategic level.
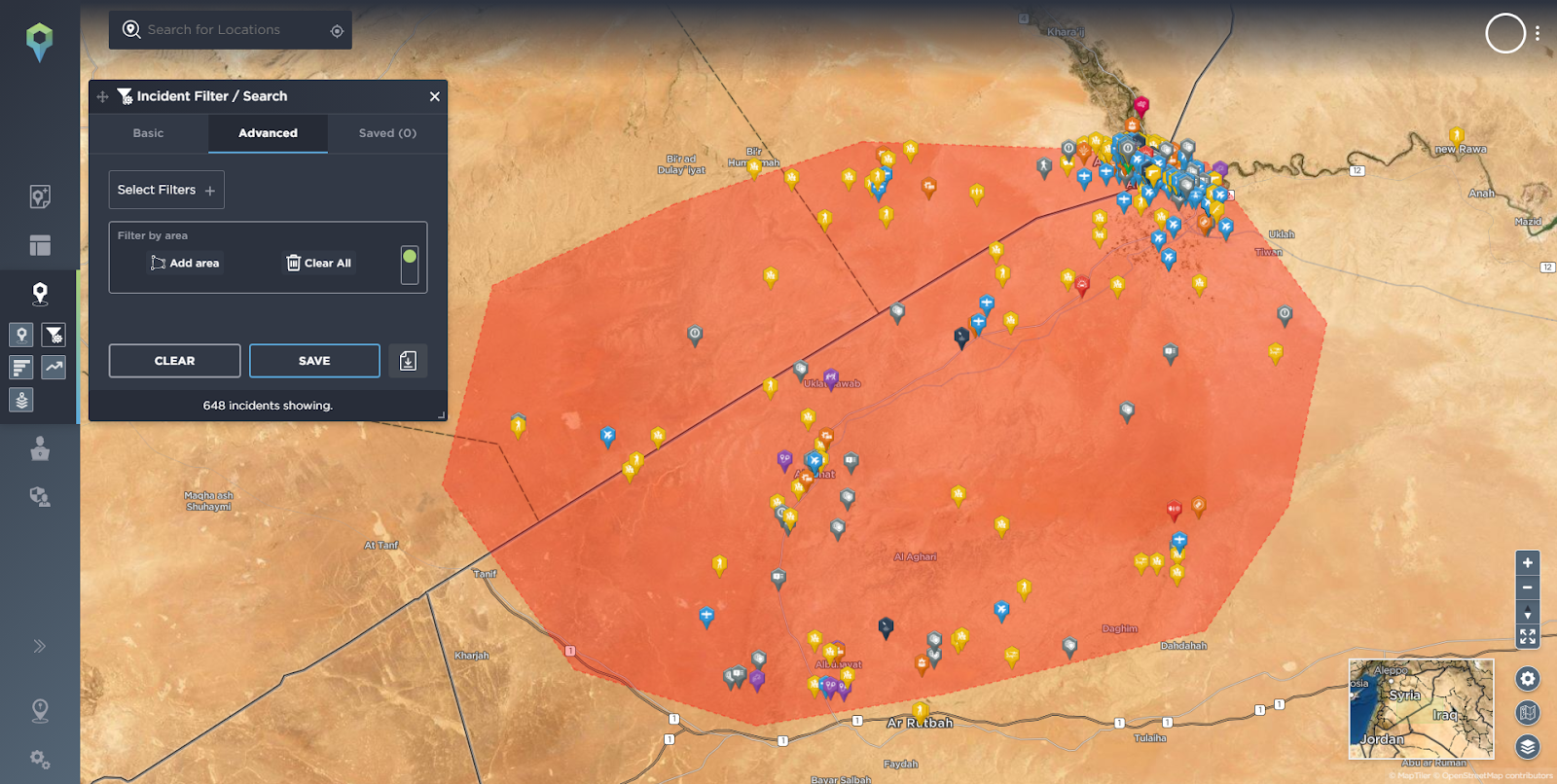
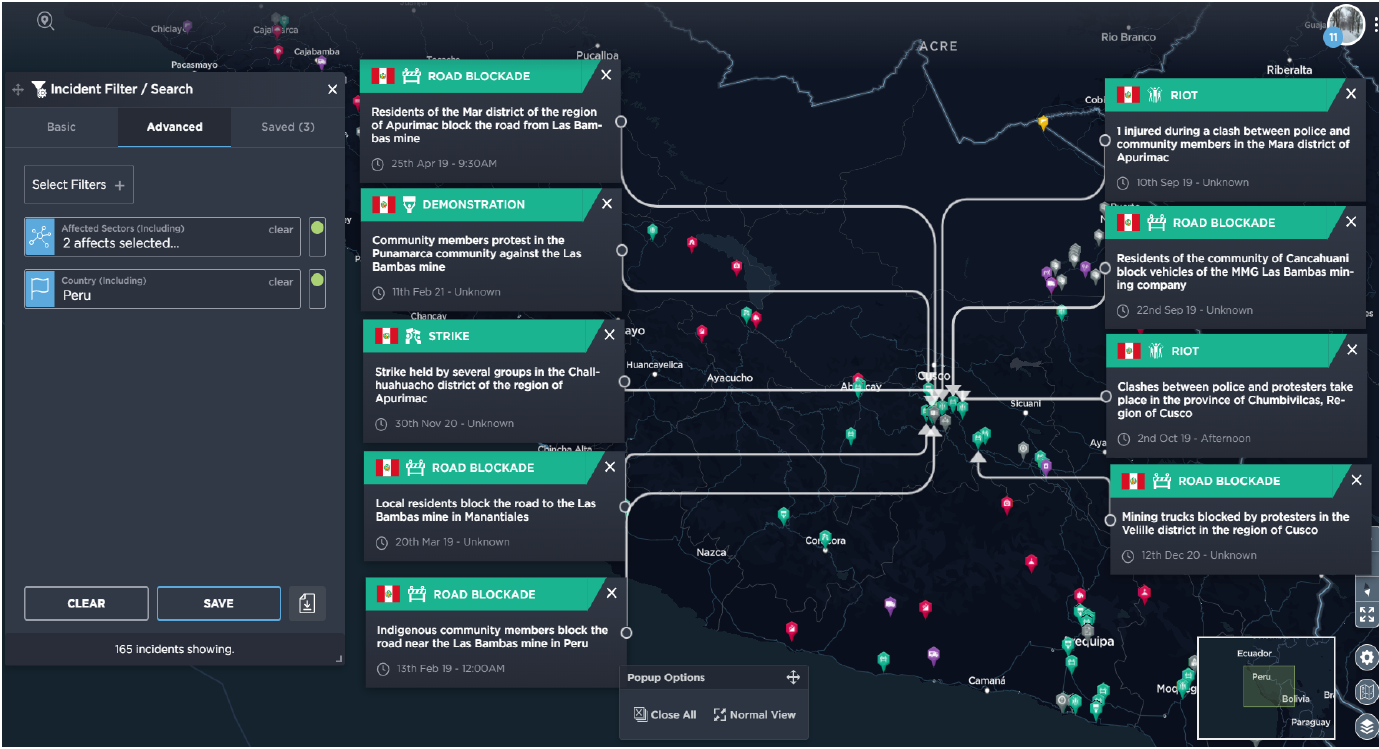
Akashat Phosphate Mine with geofence (red) drawn around the area showing incidents
Source: Intelligence Fusion
Tactical Level
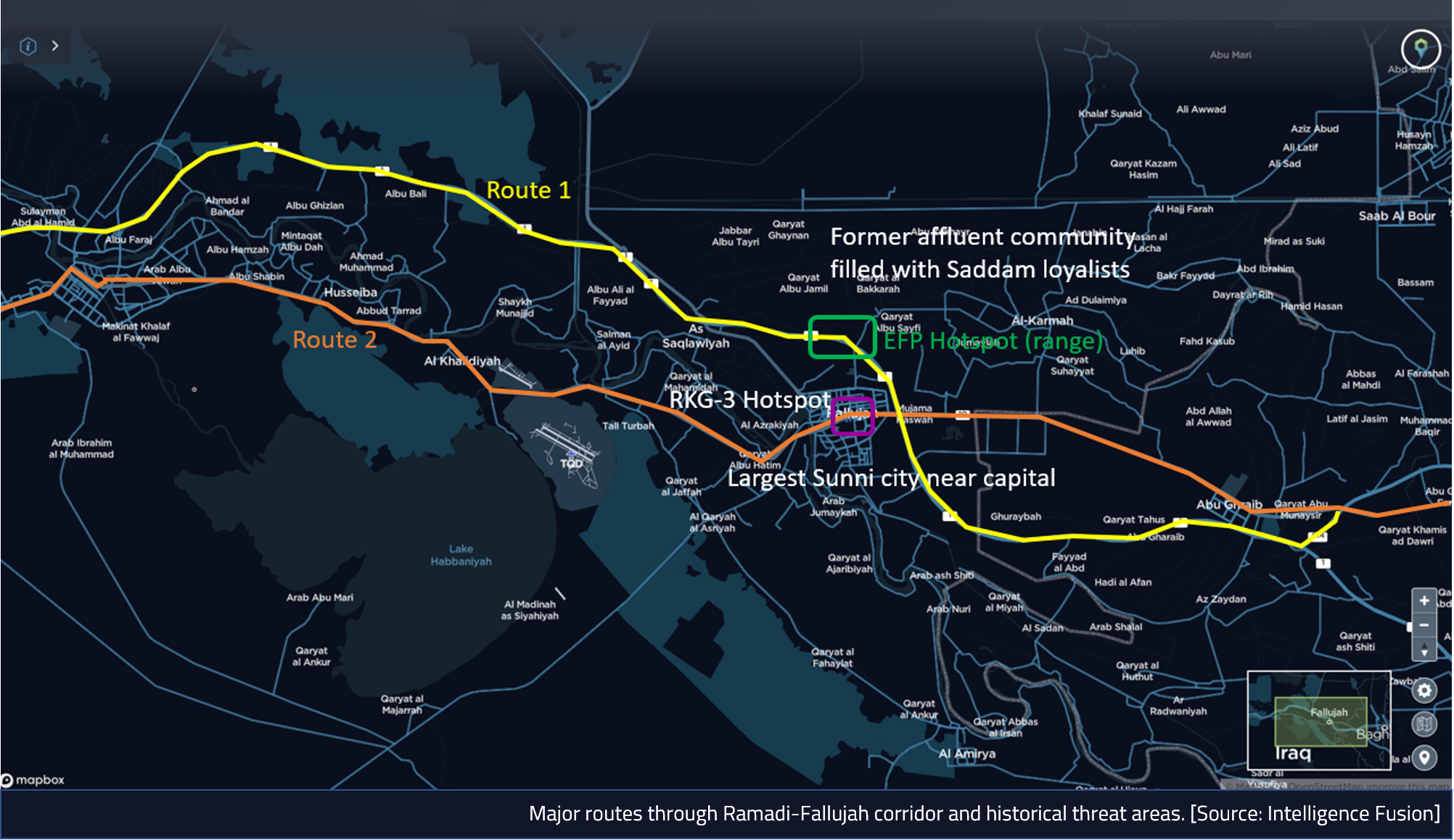
Beginning with the tactical level, we can conduct an advanced filter search and draw a geofence around the mine and review the incidents within close proximity to the mine.
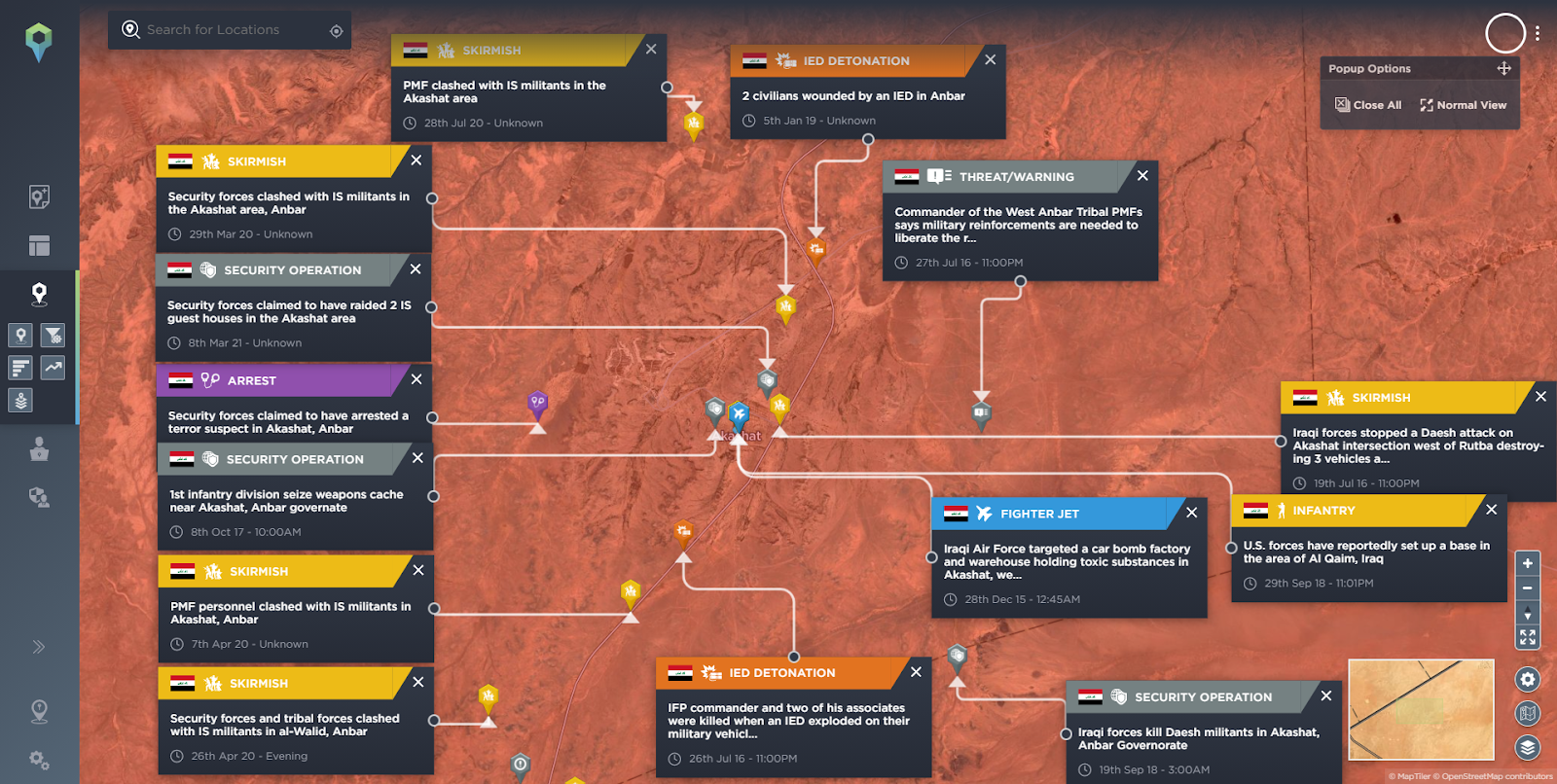
Incidents within Akashat Phosphate Mine geofence
Source: Intelligence Fusion
Looking at the incidents we can draw out context such as dates of incidents, groups involved, types of incidents, locations, patterns and trends. We can see that the most recent incident reported was on 8th March 2021, when security forces claimed to have raided two Islamic State (IS) guest houses in the Akashat area, suggesting that the threat from IS still persists. Obviously this would be key to thinking about setting up a mining operation in this area, if there is an ongoing threat from a militant terrorist group.
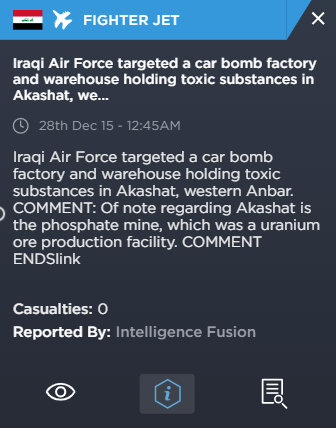
Incidents in this area involving terrorist groups go back as far as 2015, when the Iraqi Air Force bombed a car bomb factory and warehouse in the area. An analyst has also added a comment, stating that the phosphate mine was a uranium ore production facility, which is noteworthy considering the ongoing presence and historical control of the mine by terrorist groups like IS.
This also raises questions regarding the presence of unexploded ordnance and weapons which would raise a health and safety issue for any mining company looking to operate there. Just lingering on health and safety, any mining that is conducted would likely require the use of explosives, which, given the ongoing terrorist threat, would have to be secured effectively to prevent theft and misuse which would have a significant security and reputational impact for the company.
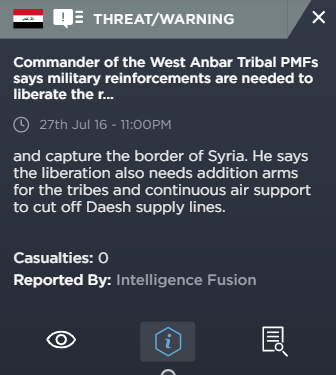
In another incident from 2016, Popular Mobilisation Forces (PMF) stated that reinforcements were needed to liberate and recapture the border with Syria to cut off IS supply lines. This tells us two things about the area that are of interest. The first is that irregular forces, PMF in this instance have been used to fight insurgents, therefore that tells us something about the capability of the country’s security forces. Also, historically this was a supply line for IS and therefore could it be again.
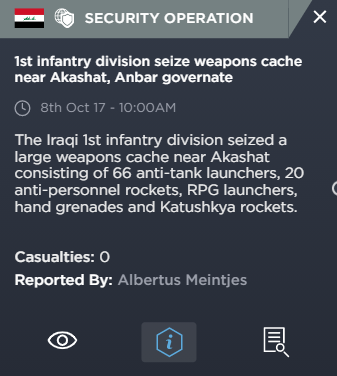
The incidents highlighted also tell us that tactically this area has been used for weapons caches and gives us examples of the types of weapons that have been used in the area – in the case highlighted above; heavy weapons, such as anti-tank weapons, hand grenades and rockets.
All of this information from the tactical level, which is quickly and easily accessible, would raise questions about the safety of setting up a mining operation in Akashat, before any in depth planning had been conducted or money spent.
Operational Level
Looking at the operational level we can conduct a basic filter search on the Intelligence Fusion threat intelligence platform for Iraq and the past 6 months.
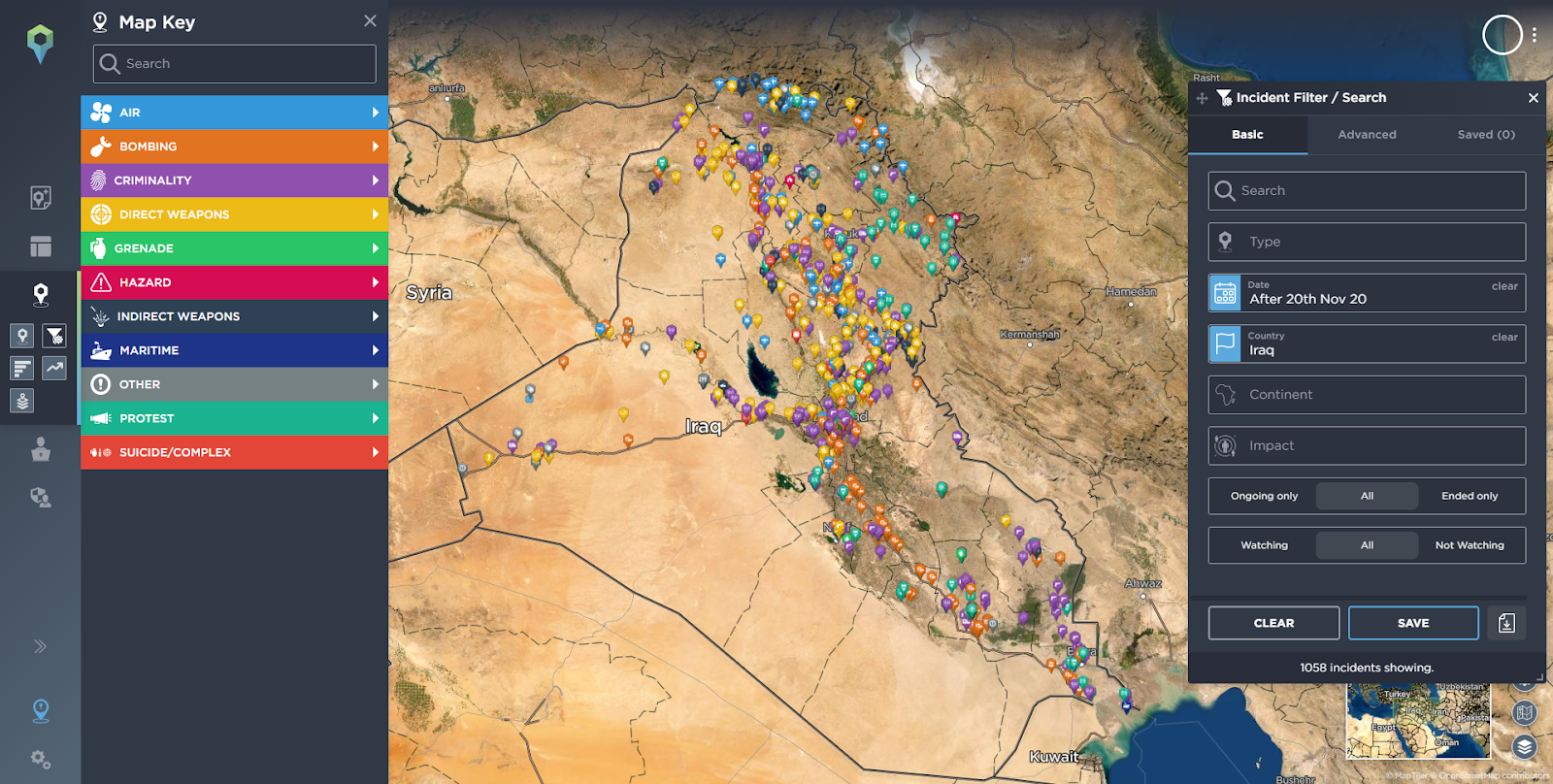
Incidents reported in Iraq in the last 6 months.
Source: Intelligence Fusion.
Because the icons are colour coded based on type and the incidents are, wherever possible, geolocated accurately, we can get a snapshot of the types of incidents that are occurring in Iraq and where. We can see incidents of protest (turquoise) across the country but especially focused in the South, Centre and North East of Iraq. Direct weapons incidents, conflict type icons (yellow) are commonplace, especially in the centre, North and West of Iraq. Criminality (purple) is prevalent across the country. Bombings (orange) are also prevalent across Iraq, but especially on main routes, especially running from North to South towards Baghdad. Finally, whilst there aren’t as many Suicide/Complex (red) incidents as seen in previous years, they still do occur and are located not in major population centres, but slightly outside, suggesting that security forces are protecting cities and towns fairly succesfully.
Strategic Level
Finally, looking at the strategic level, we can use the basic filters to search for the last six months’ incidents, and filter for the continents of Asia, Africa and Seven Seas. This therefore gives us the wider regional intelligence picture, including maritime issues.
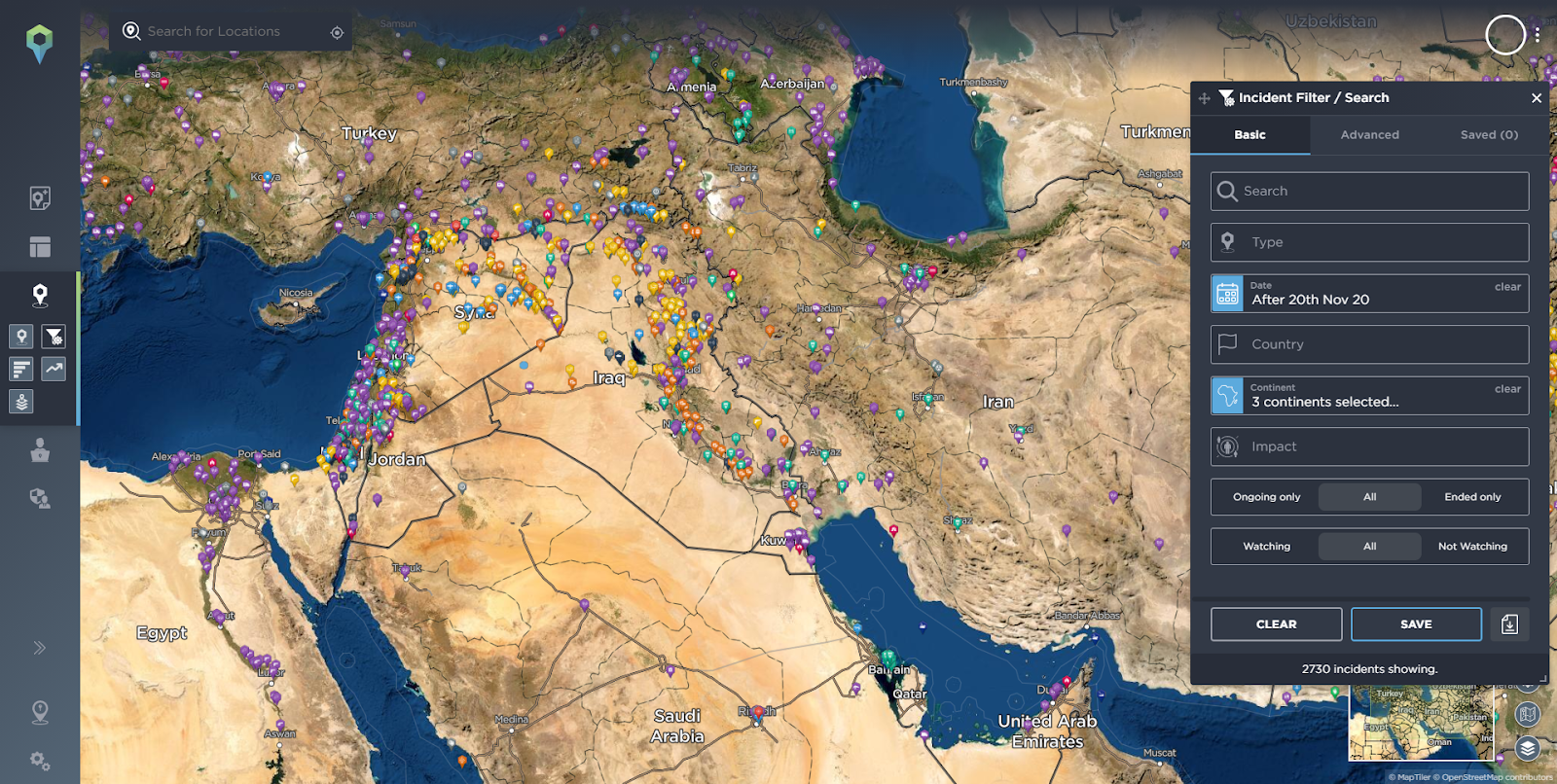
Incidents reported in the Middle East in the last 6 months.
Source: Intelligence Fusion.
From a strategic perspective you can see that the conflict in Syria is still ongoing and IS still has a presence across the border near Akashat. The wider Middle East has seen a deterioration in the security situation with Israel conducting an offensive against Hamas.
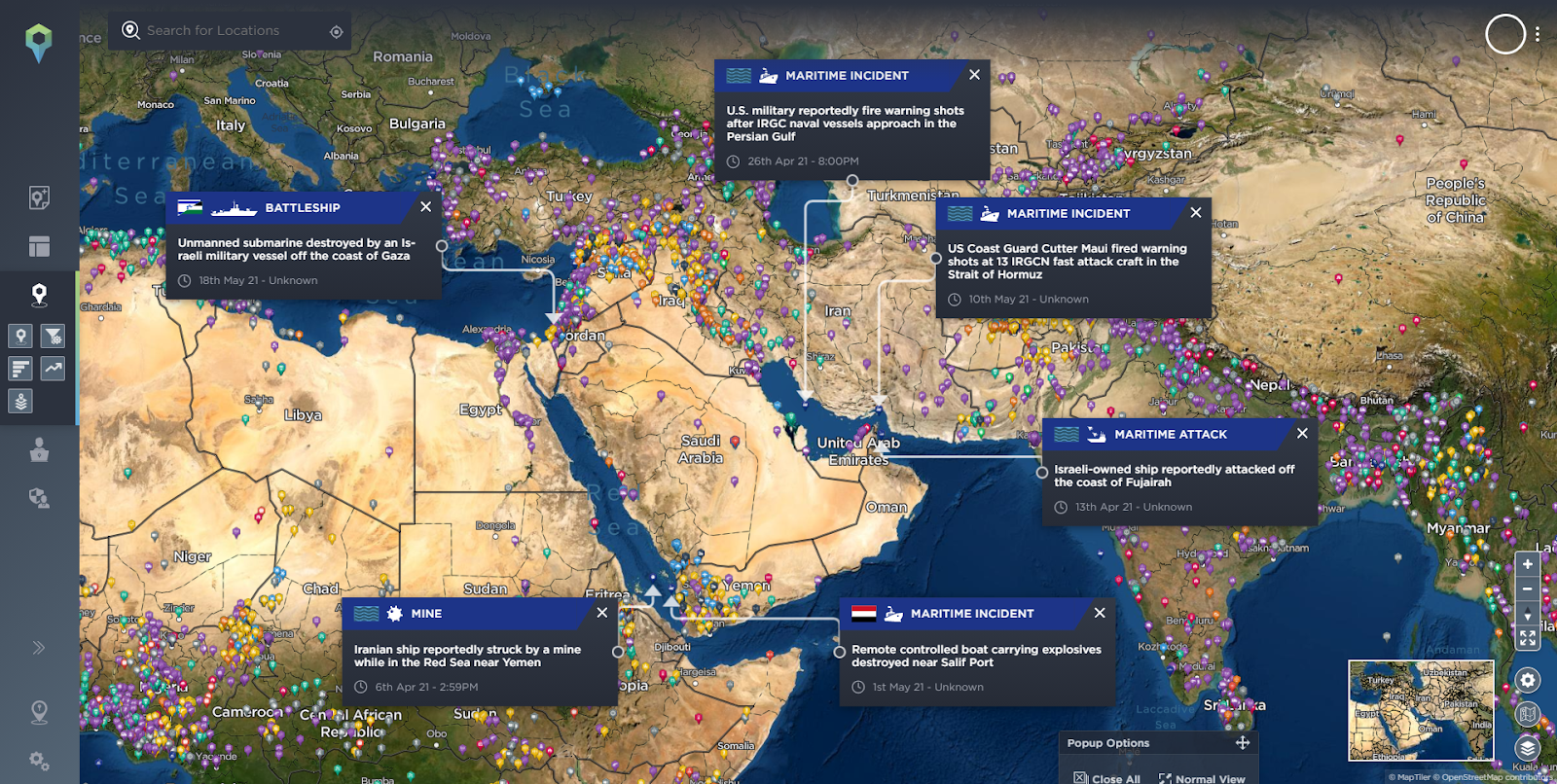
Maritime incidents in the Middle East and Africa in the last 6 months.
Source: Intelligence Fusion.
There is also a spike in tensions between Iran and Israel, especially involving attacks on ships.
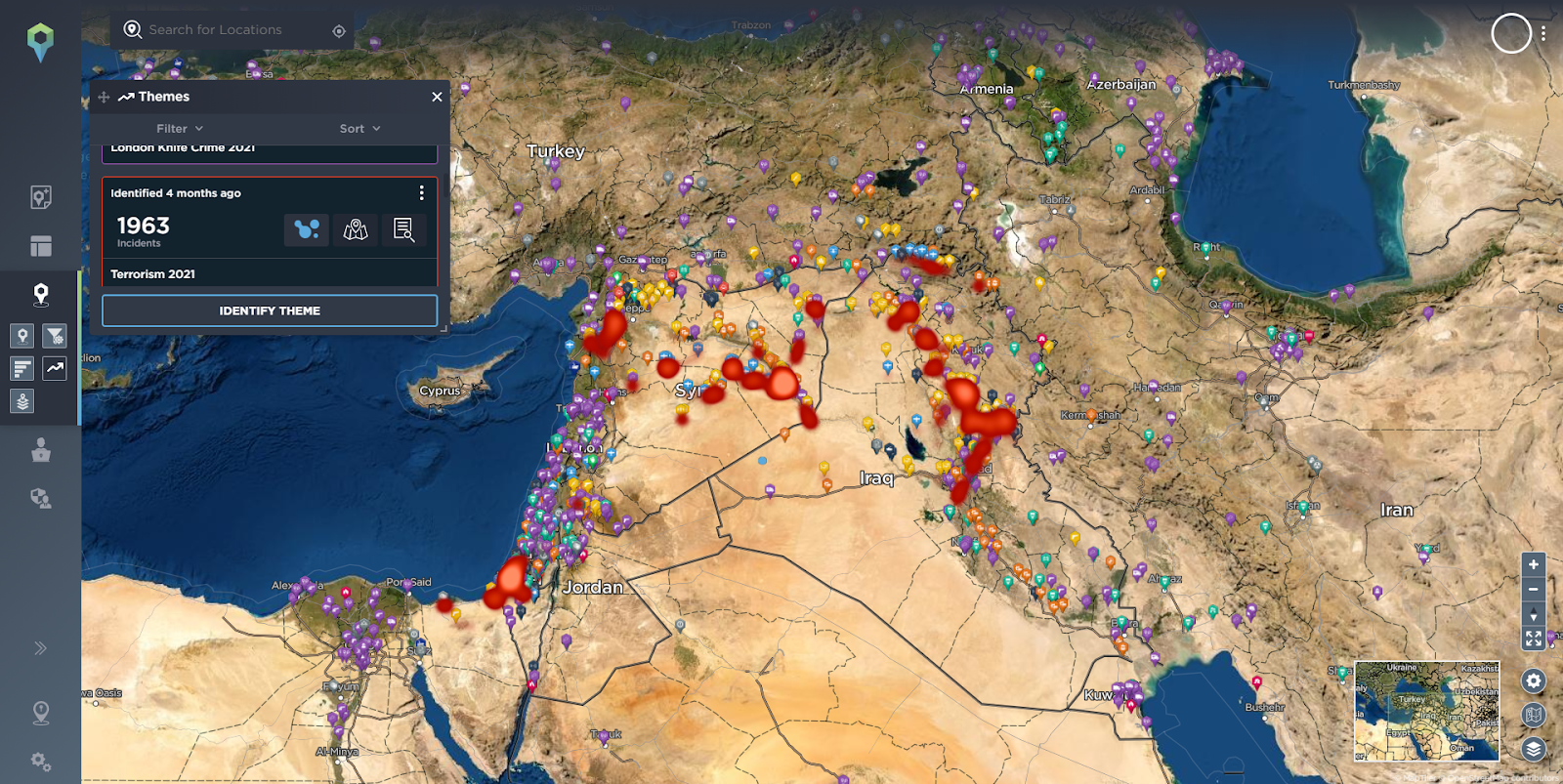
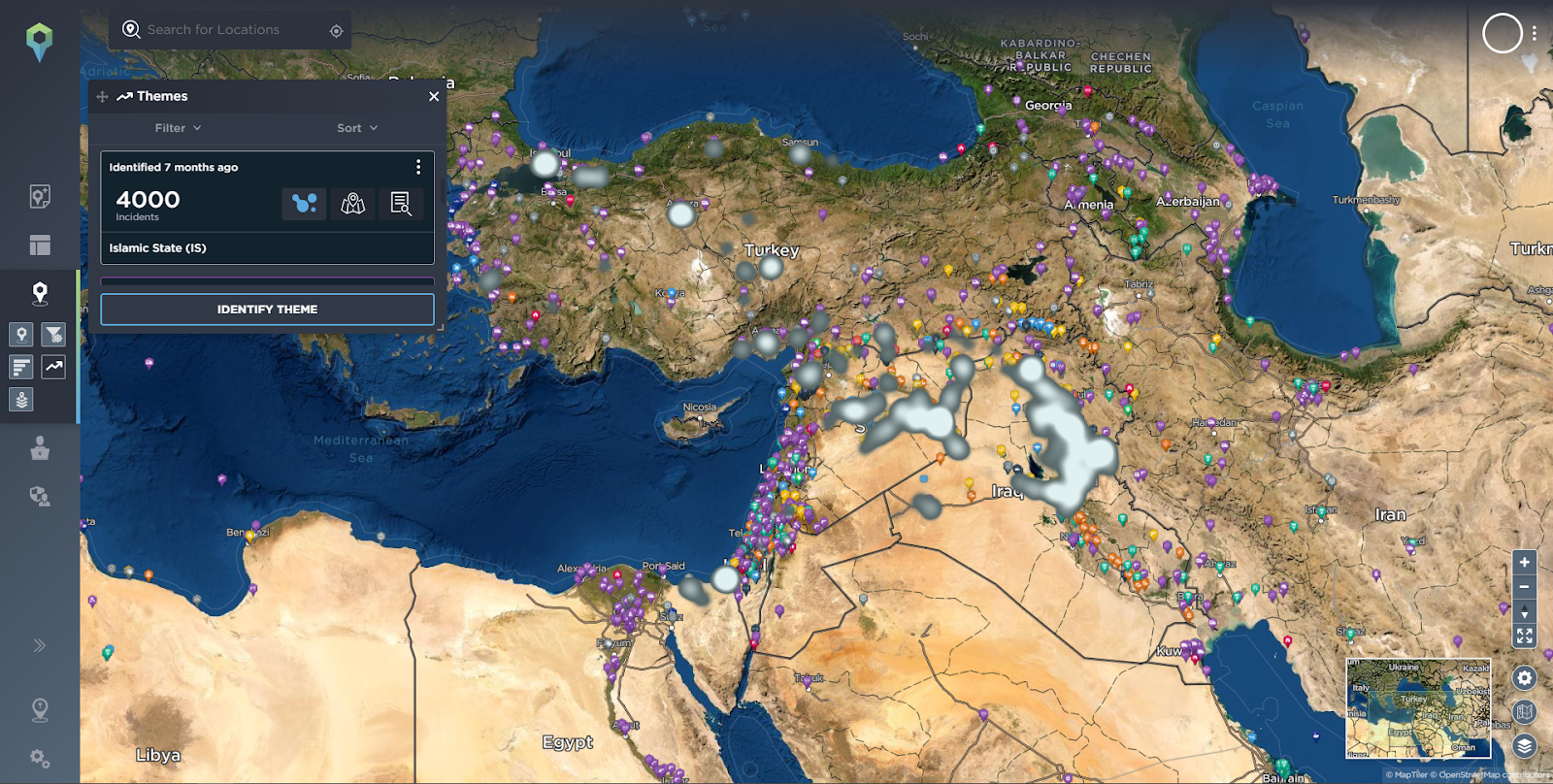
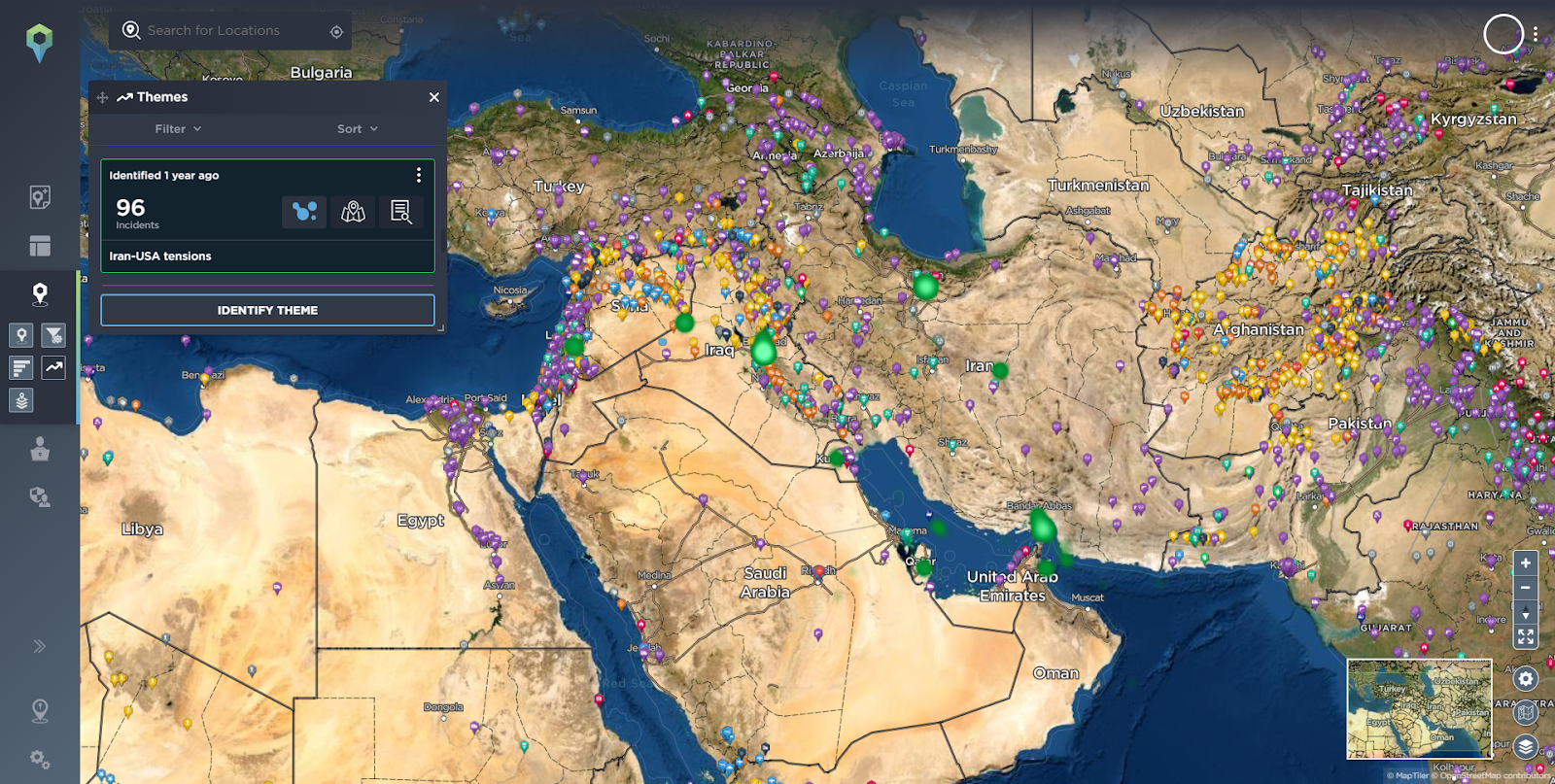
Using our themes functionality we can also easily visualise via heat maps topics that have been identified by our analysts, such as Terrorism in 2021, Islamic State related incidents or the tensions between Iran and the USA.
Without going into every geopolitical development, conflict or theme, the point here is that from the incidents on the ground in the local proximity of a mining operation, up to the country and regional level, by using threat intelligence tools you can quickly and easily identify the threat landscape, as well as how it may impact mining operations.
In terms of accessing tailored intelligence, you can even go one step further in the platform. By conducting an advanced filter search for the [Affected Sector] filter and selecting [Mining] you can then see specific incidents that have impacted the mining sector.
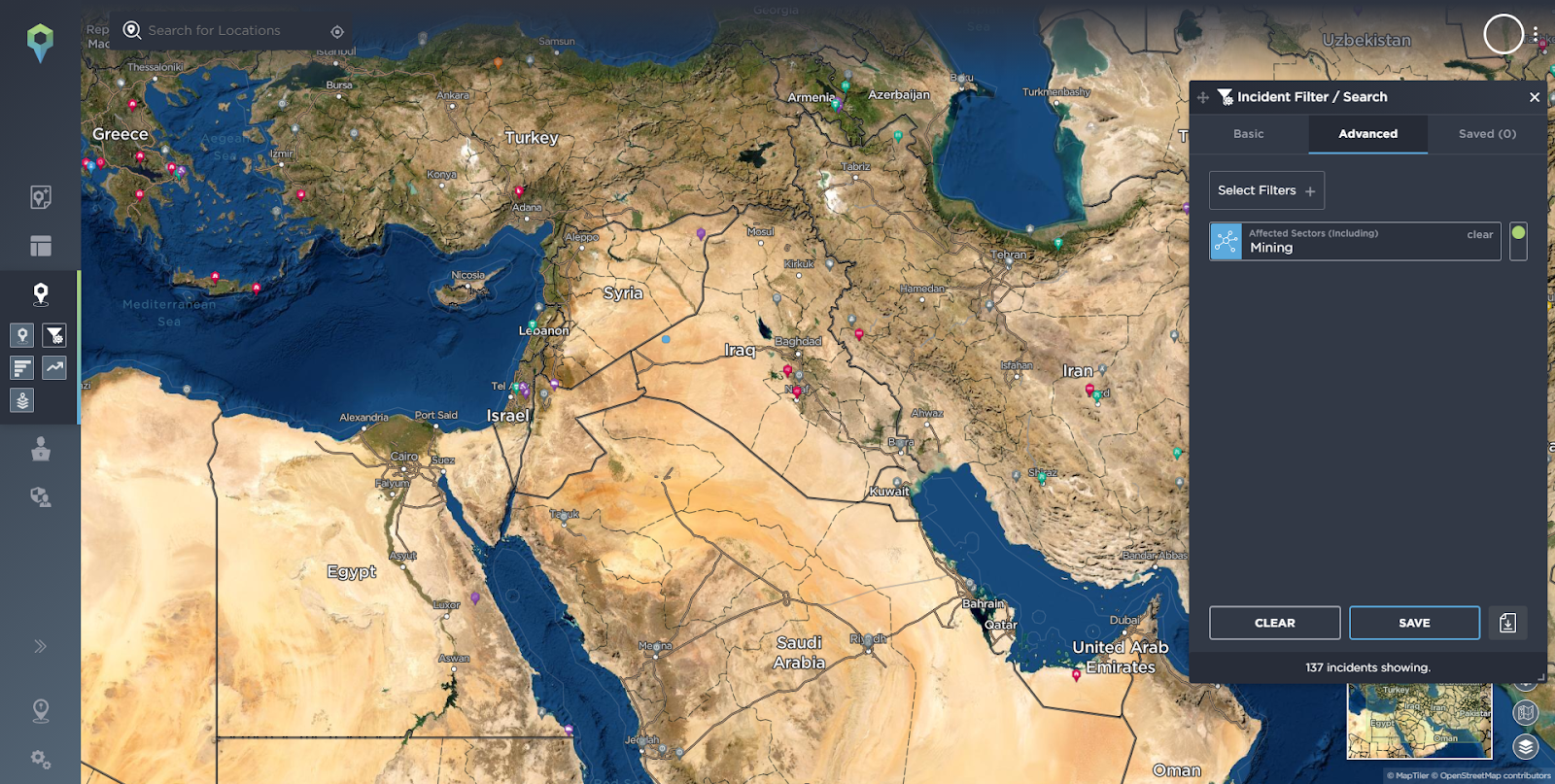
Affected Sector filter with Mining sector selected.
Source: Intelligence Fusion.
All of this information, in this instance, would likely point to Akashat Phosphate Mine being a location that is too high a threat to be mined. If, though, the threat was more tolerable to the company, the intelligence provided would add vital context in preparation for Prospecting/Exploration, informing the ways in which the first step of setting up a mining operation can be done as safely as possible.
Mine Design and Planning
Once prospecting and exploration has been conducted and the company is confident that there is an opportunity, the next step is to move on to the mine planning and design phase. In this phase, the company will likely draw up multiple plans to mine the material over a decade or two decades in order to estimate financial implications. The planning also looks at how the project can be carried out in a safe, environmentally sound, economically viable and socially responsible manner.
In addition to the threat intelligence previously outlined, there is additional context that can be provided by intelligence providers that could feed into this planning. Intelligence analysts often conduct a process called Intelligence Preparation of the Battlespace (IPB), and similar methods of analysis could be used when looking at mining operation security. IPB is a systematic, continuous process of analysing the threat and environment in a specific geographic area. It is designed to support decision making. Factors intelligence analysts can look at which would impact the running of the Akashat Phosphate Mine are things such as:
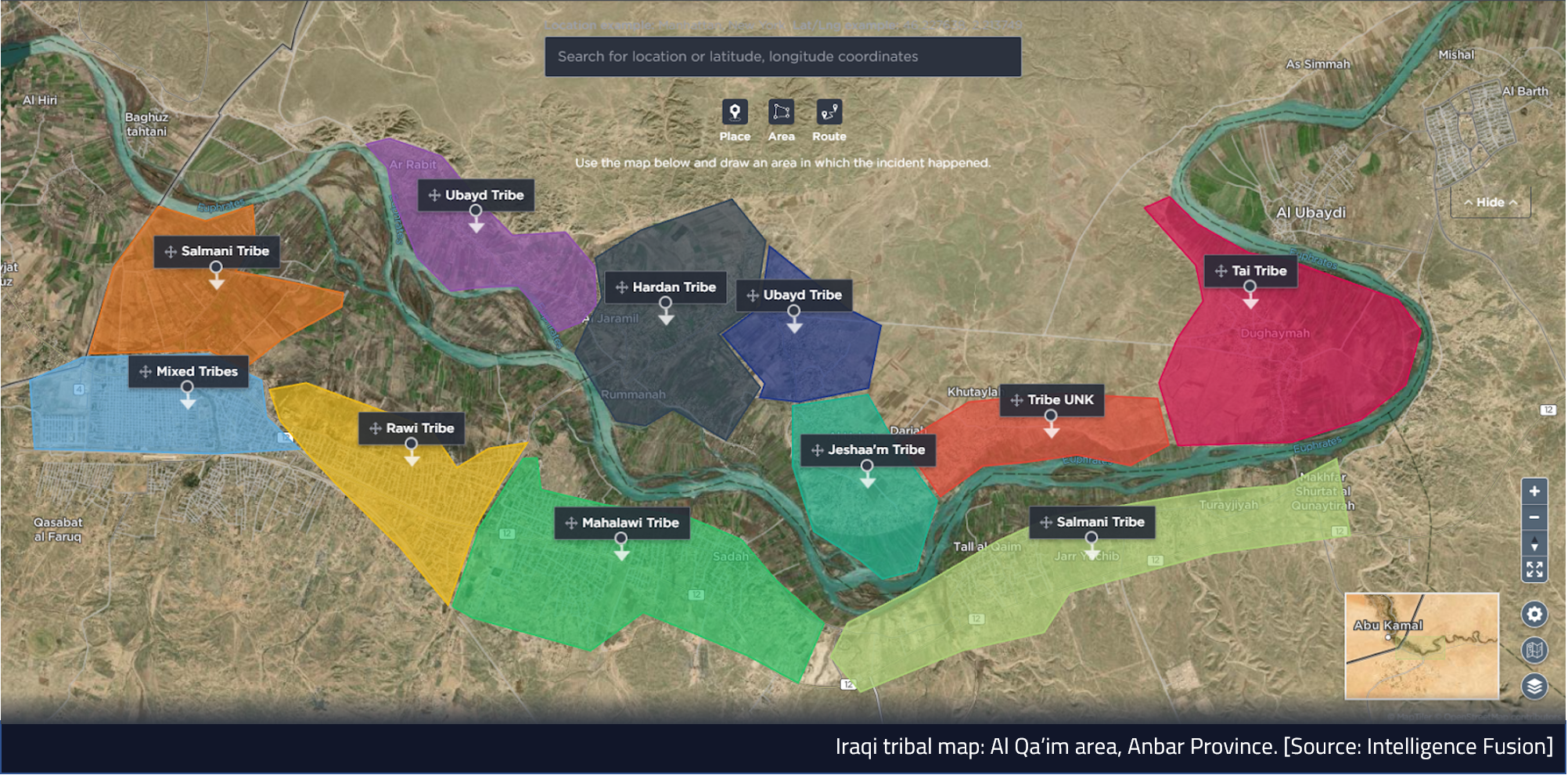
- Population status – The local population would likely be required to operate the mine, therefore how large is it? Also, what is the status of tribes in the area and who are key leaders who would likely have to be engaged with to ensure the smooth running of the mine?
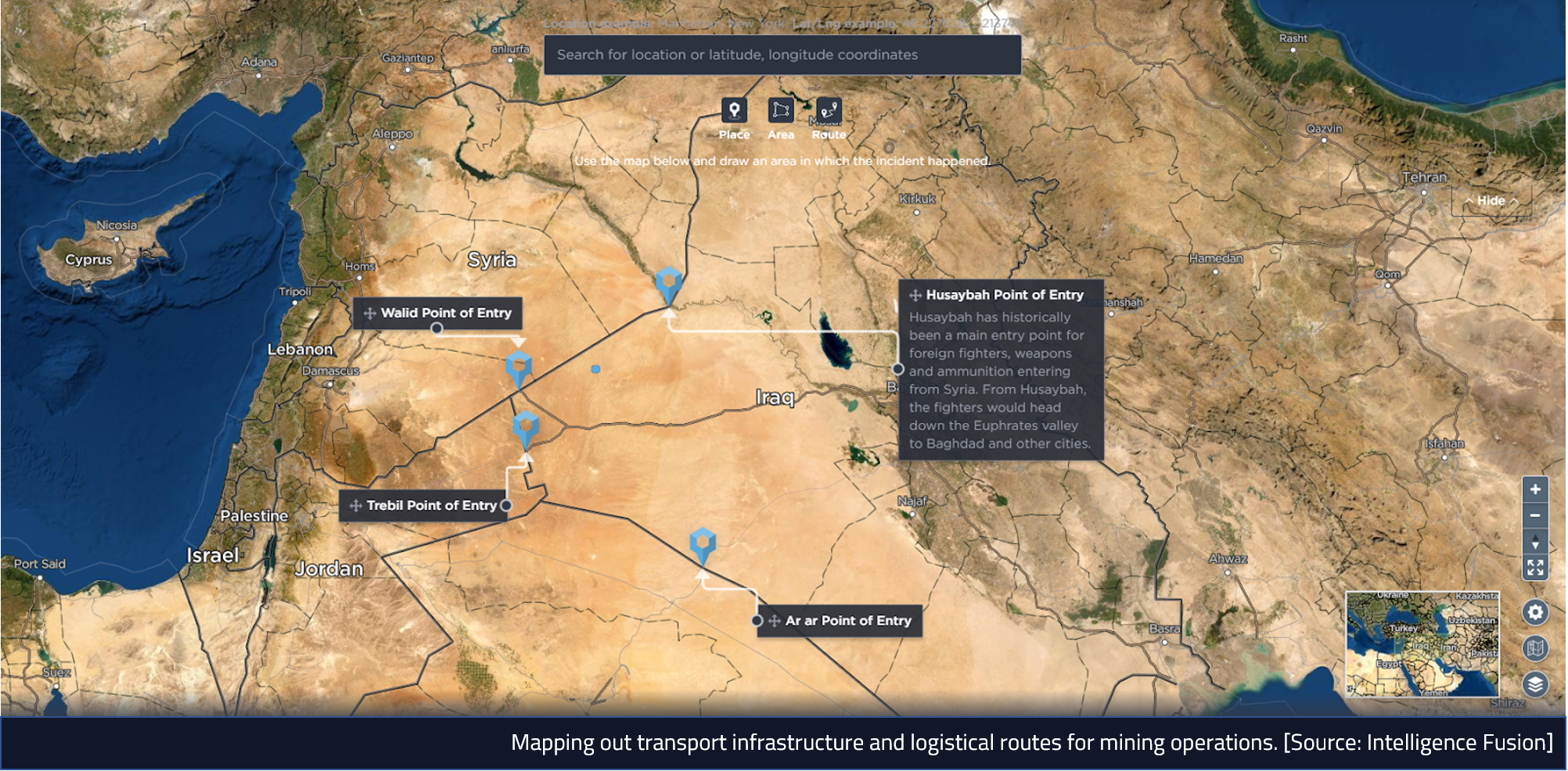
- Infrastructure – Mapping out transport infrastructure and logistical routes.
- Opposing forces – Historical threat context.
- Friendly forces.
- Political or socio-economic overlays.
All of this information would provide insightful context for the mine planning and design phase, helping to ensure that any planning conducted is based on facts rather than assumptions, helping to make the plan as effective as possible, whether it’s for operating an existing site like the Akashat Phosphate Mine or for putting a plan in place for opening new mines.
Mine Production
Once the mine planning and design phase is complete and the relevant authorities have been granted the mine moves on to production. During this phase, mine buildings and processing plants are built, and any necessary equipment is obtained. The operation of the mine to recover the ore begins and continues as long as the company operating the mine finds it economical to do so. This is where companies should have an effective, long-term, flexible plan for mining site security – as the operation is scaled up, the threat profile changes because of increased exposure of assets and personnel. Your threat intelligence plan should account for this change in threat profile, and be ready to be scaled up alongside your operations. Security forces are likely increased to support the operation, but also the insider threat becomes a significant issue through the hiring of staff. Also as Production begins the operation comes under greater scrutiny from the local population, who will likely look to receive some financial incentive due to the mining operation making use of the local natural resources. You can read our post about Community Engagement here.
All throughout this process, the mining operation needs to keep up to date with the tactical, operational and strategic intelligence picture. For example, what if IS rises again, beginning in Deir ez-Zur which is across the border of Akashat in Syria? The mining operation will need to track this carefully, because at what point might the mining operation come under threat? This will be balanced against the security posture of the mine and the status of local security forces. What local issues are the population facing and can the mine engage with them sooner so they are seen as part of the community rather than an entity just removing resources without appropriate compensation? What is the crime profile of the area and how is it changing? With the arrival of a mining operation, it will likely become a target for criminals. How is the terrorist threat changing in the area? Is this mining operation now seen as a target? Potentially, especially depending on the company’s nationality.
Constant, tailored situational awareness is absolutely critical to the safe running of a mining operation and for a relatively modest cost. Intelligence Fusion is aware that our clients’ threat intelligence requirements change as their businesses or operations change. This is why we update our Intelligence Collection Plans (ICP) to meet their changing needs and ensure that their intelligence continues to be tailored to their exact requirements. You can read more about tailored intelligence here.
Closure and Reclamation of Mines
Finally, the last phase of the mining process is closure and reclamation. A comprehensive mine rehabilitation program aims to ensure public health and safety, minimise environmental effects, remove waste and hazardous material and preserve water quality.
From a security perspective, this is likely a more exposed period for the mining company when the company’s footprint reduces, perhaps local workers have been laid off creating hostility, or there are worries about the environmental impact of the operation. Throughout this process the situational awareness that was in place should continue, especially to keep track of the tactical intelligence picture and how the mine’s closure is impacting the local community.
Summary
Threat intelligence should therefore play a vital role in all areas of a mine’s operations. It should form a key part of your initial planning, before any prospecting or exploration is even attempted, to get a full understanding of the threat picture and what risks you might face, and determine the feasibility of operating in the area. But once this has been done, the additional contexts and level of situational awareness provided by threat intelligence can prove vital to the design and planning of the mine site and wider operations, to ensure an effective security plan, and a set-up that can mitigate or reduce the identified risks as much as possible. This is just as true once production is underway, which brings added exposure and risks to your assets and personnel, and added scrutiny from the local population – making a high level of up-to-date intelligence a necessity in order to accurately assess the ongoing threat level and plan accordingly.
Intelligence Fusion has worked with clients in the extraction industry to help them monitor and manage historical and ongoing threats to their business, assets and people. Our threat intelligence platform contains a database of more than 1,200,000 historical incidents, with 20,000 new incidents mapped every month – allowing our clients to gain a deep understanding of the threats facing particular areas of operation and specific industries and increasing their ability to see any potential forthcoming areas of risk to their activities.
Whether you’re in the process of setting up a mining operation or would like to know more about how threat intelligence can help improve the security of your existing operations, get in touch with a member of our team.