In addition to the types of threat intelligence that is available, there are several different types of intelligence solutions too.
Depending on your current set up and budget, you may just require the data. For example, if you have an existing platform or interface that you can use to visualise the data, you can ingest threat intelligence API feeds into your software to enhance or improve your current dataset.
If this isn’t the case, your best option is to look into threat intelligence platforms. This solution will not only provide you with the data itself, but the best software solutions will help you better interpret the information and provide perspective through intuitive intelligence tools and powerful visualisation capability.
How do you know the best solution for you? Typically, you’ll find that the biggest difference in threat intelligence providers is the way in which they collect and gather the data.
Automated Collection
The meteoric rise of artificial intelligence and machine learning tools has changed the way many industries operate – security and intelligence being one of them.
In order to increase the speed of gathering data, and reduce the overheads of hiring a team of expert analysts, many intelligence providers have introduced automated collection.
Algorithms are built to comb through news articles and social media feeds from around the world to monitor trends, geopolitical developments, and potential crises in real-time. Tools such as natural language processing are utilised to assist machines to compute the meaning of words and provide context in the same way that humans do. The end product is large volumes of very fast data being fed to the users.
Threat intelligence solutions that solely rely on automated collection are usually configured so that the algorithms identify key words or phrases on social media. Any tweet or post containing that trigger word will activate an alert.
It goes without saying that there are many benefits to this kind of threat intelligence software, however, a purely automated solution can also have it’s drawbacks too.
Without any human involvement in the collection process, there’s very little analysis or context. The data is in its most raw format, so unless you have a team of analysts on your team who can weed out the most relevant alerts, it can be overwhelming.
Analyst-led Collection
With an analyst-led intelligence solution, the data collection is manual. There will be a team of analysts identifying and processing the data they gather, which is then disseminated via a threat intelligence platform.
The best intelligence providers will hire analysts who will likely have built up years worth of expertise in the region or specialism that they cover. They’ll be able to provide unparalleled context to incidents and provide additional insight into the ‘so what’ factor of intelligence – essentially, why is this incident important and what does it mean to you?
By helping you to answer these questions, you can save time, effort and resources interpreting the data on your end. Analyst-led collection can be particularly beneficial if you have a small team or if risk analysis is the main use case for your business.
If you’re looking at threat intelligence for incident response, an analyst-led solution may not provide you with the timeliness required to meet your objectives, unless the provider is focussed on one particular area.
Hybrid Collection
Both speed and context are important to provide the most accurate and actionable threat intelligence. At Intelligence Fusion, we’ve taken a hybrid approach.
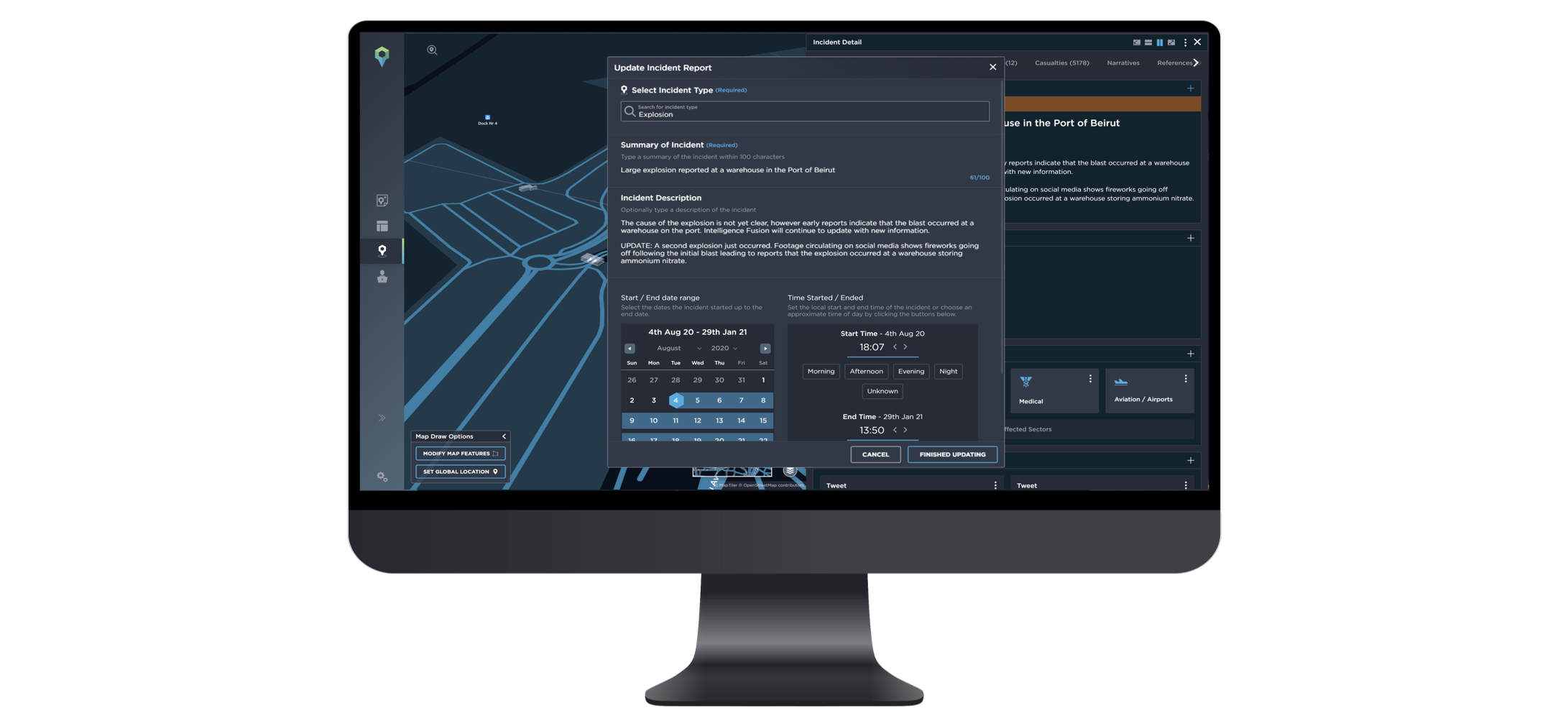
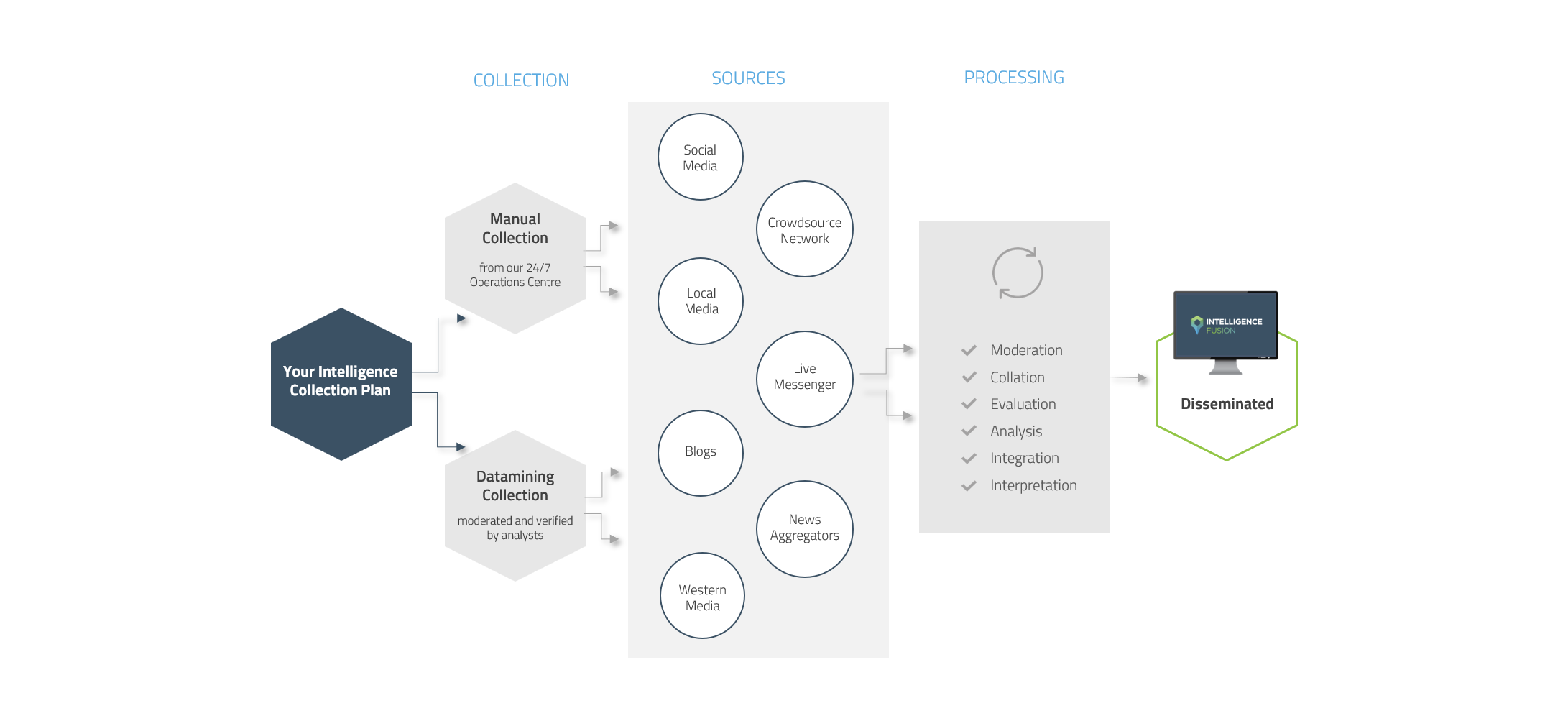
We’ve built a team of military-trained analysts, who operate our 24/7 Operations Centre. Their job is to gather, evaluate and assess information, but they’re supported by data scraping tools which were designed to better identify incident details across the internet. By fusing automated collection with the expertise of our analysts, we balance speed and accuracy to provide the most valuable overview possible.
All of our data is verified, carefully geolocated as well as contextualised to provide you with practical, valuable intelligence that you can view in our award-winning platform.