Protect Your Business: Unveiling the Top Physical Security Threats to the Telecom Industry
Analyst intelligence has revealed the top 5 threats facing the telecommunications industry today based on open-source data.
Physical security threats are a prominent risk for many of our telecom clients, with increased activism and vandalism as well as unpredictable severe weather conditions – natural and man–made threats impacting the telecommunications industry are vast.
We are here to support your reporting; our analysis of the global threat landscape allows us to report on a wide range of incidents linked to the telecom industry. We help our clients to better protect their operations by receiving real-time updates, analyst insight and having access to over 1 million historical data points.
Vandalism, Sabotage and Activism
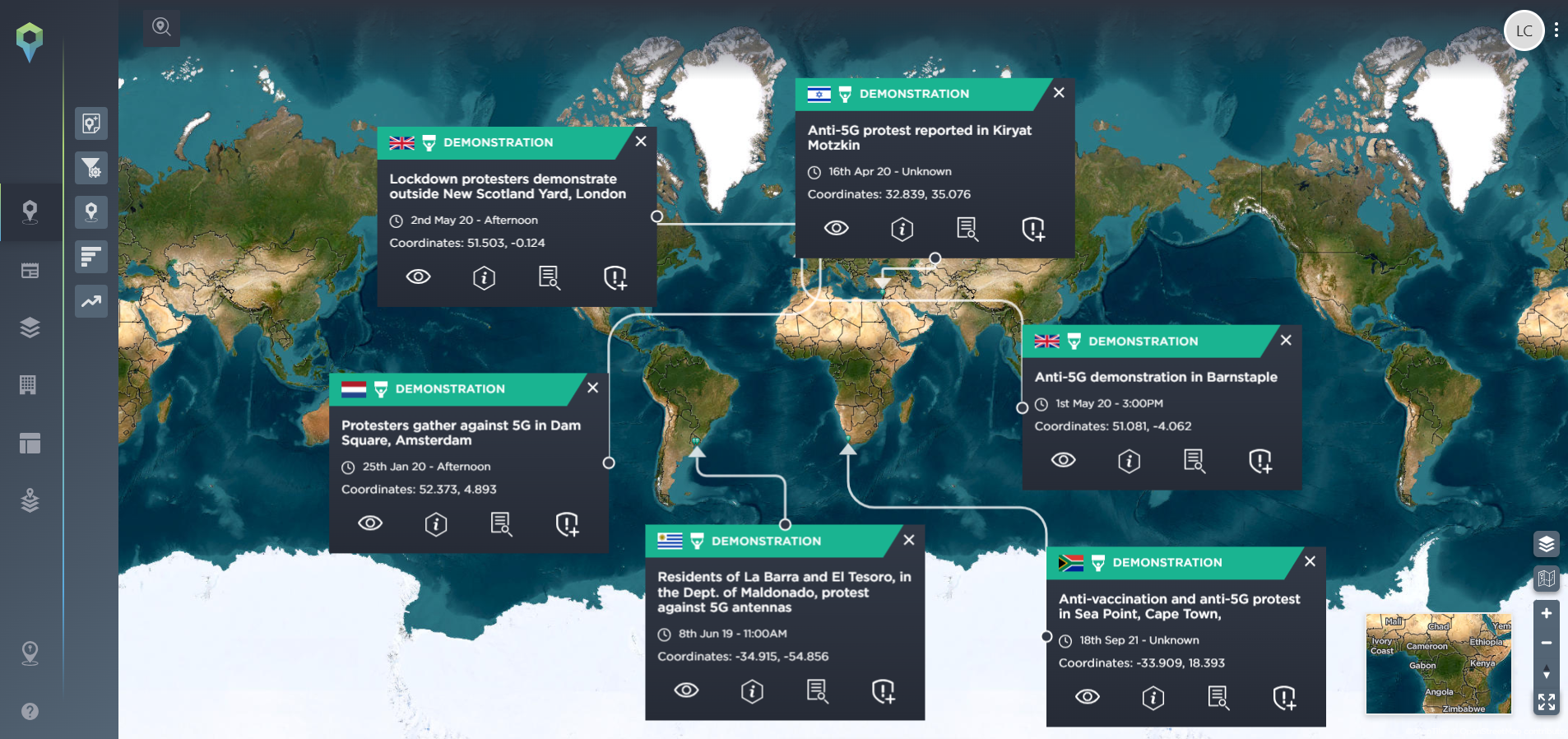
In recent years attacks on 5G towers and phone masts have been prevalent. Conspiracy theories spread on social media channels escalated the threat level, with many social media sites having to delete pages and posts encouraging vandalism of phone networks.
Social media has also been used as a tool to spread activism and fake news about 5G technology being dangerous. This has resulted in bigger groups gathering and more disruption being caused. Protests have been widespread across the globe with varying degrees of severity.
Phone network operators are said to be particularly concerned about the safety of their staff, with members of the public harassing them and filming encounters to share on social media.
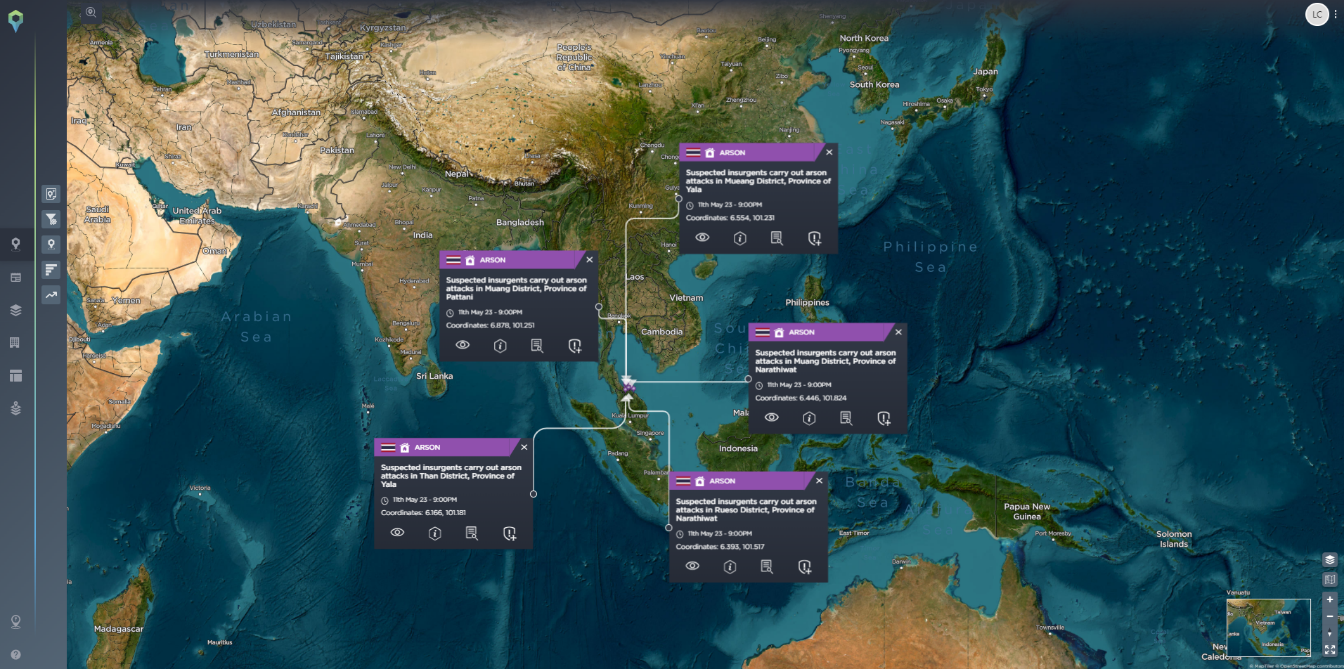
In the past few years, most attacks have taken place in Western and Northern Europe as well as Western Africa. However, since the start of 2023, the most prominent location for telecom tower attacks has been Asia, particularly Thailand and Pakistan.
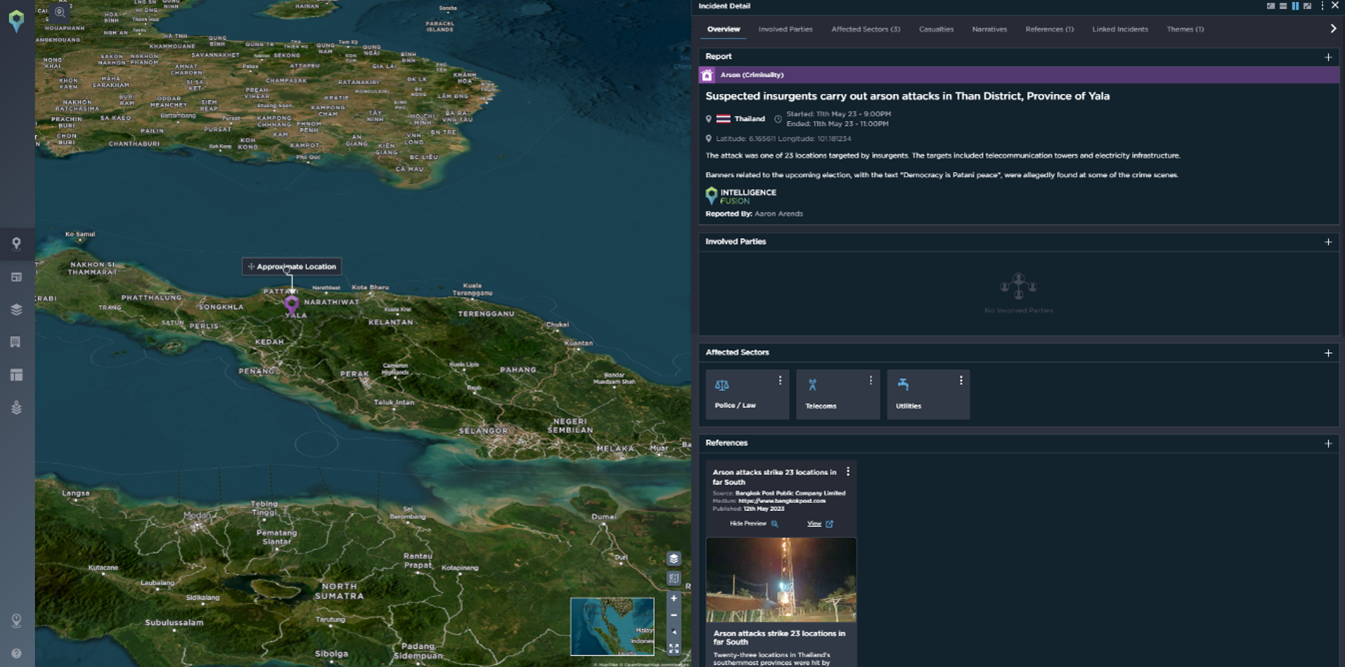
In May this year, 23 locations were targeted by insurgents in the deep south of Thailand in the lead-up to the general elections. The targets included telecommunication towers and electricity infrastructure. The politically motivated attacks occurred in areas where tensions were boiling over as it has increasingly become violent due to drug cartels, oil smuggling networks, and sometimes pirate raids.
Banners related to the upcoming election, with the text “Democracy is Patani peace”, were allegedly found at some of the crime scenes.
Advanced search on the Intelligence Fusion platform allows clients to quickly identify threats relevant to them. In addition, mapping static assets allows clients to create geolocations around their assets, meaning they get alerted as soon as an incident occurs within a certain radius of their sites.
Theft/Burglary
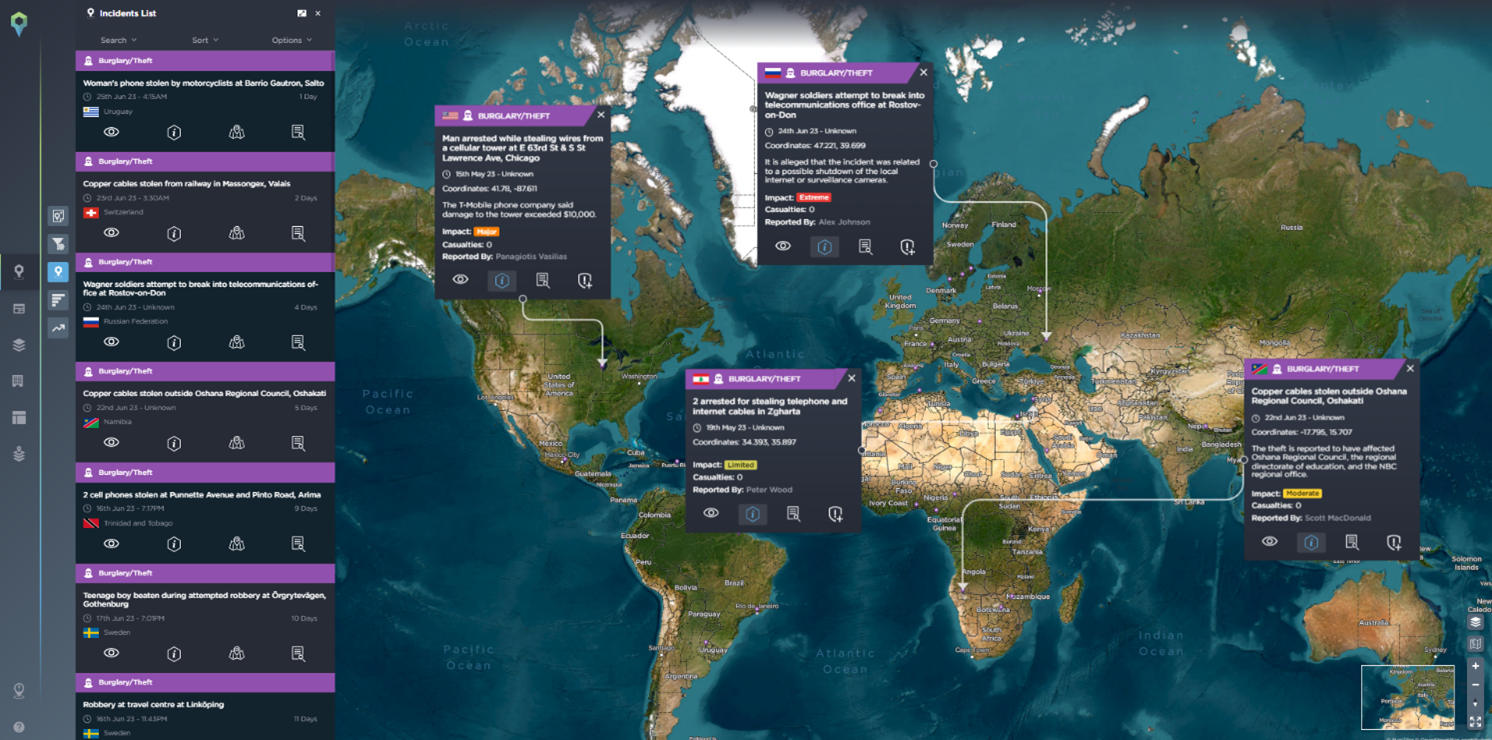
Telecom infrastructure and equipment, including copper cables, optical fibres, and network components, can be attractive targets for theft due to their high value. Theft is widespread and is not particularly limited to specific geographic areas. In the last couple of months, there have been multiple occasions of copper cables and other telecoms infrastructure being stolen in various countries disrupting services and causing financial damage to companies.
Major bouts of political unrest have also highlighted that telecoms are often heavily restricted in times of unrest or insecurity. In Iran, for example, the government routinely shuts down online communication during protests in major cities. More recently, Wagner forces reportedly attempted to break into telecommunication offices in Rostov-on-Don in relation to an attempted shutdown of local internet and surveillance cameras. Click here to learn more about the Wagner Group Mutiny and the events that unfolded.
All incidents mapped on the Intelligence Fusion platform are verified by our expert analysts, ensuring only accurate information is provided.
[Image Source: Intelligence Fusion]
Terrorism
Telecom infrastructure is considered critical infrastructure, making it a potential target for terrorist attacks or political activism. This not only disrupts services and causes economic damage but also impacts public safety and security.
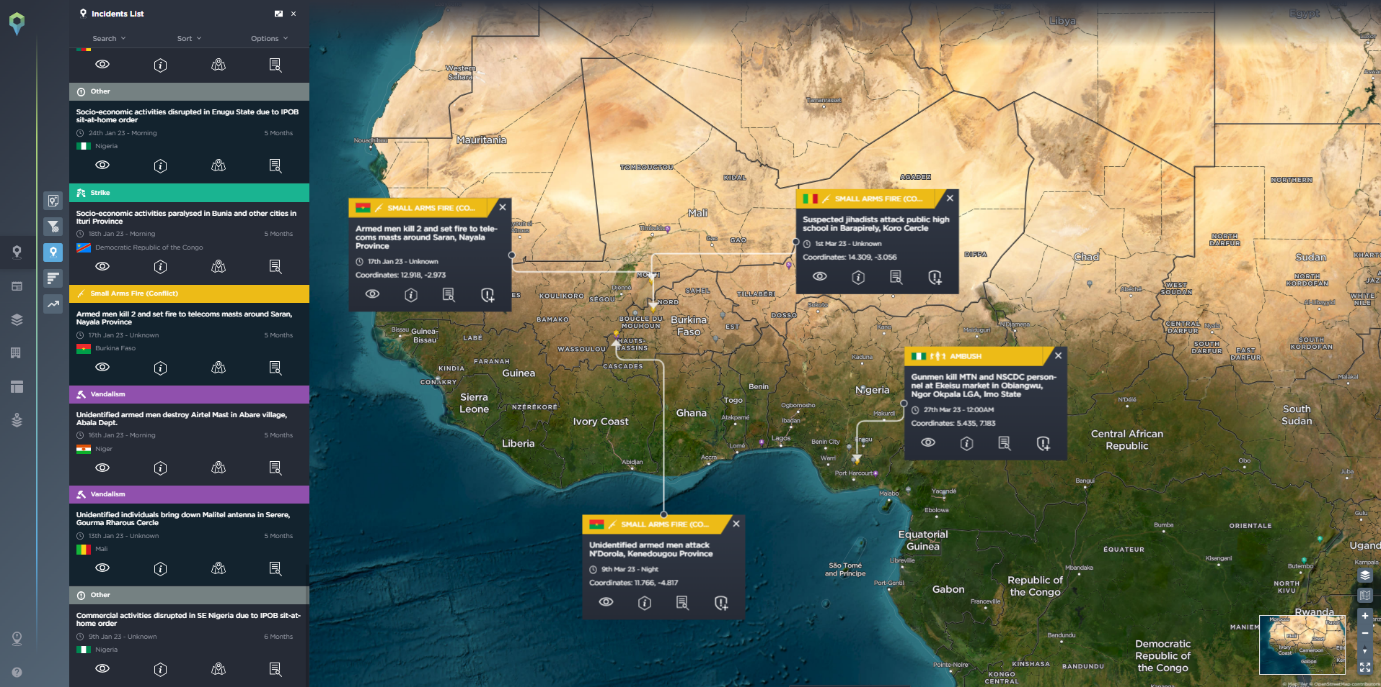
West Africa is a particular hot spot for this kind of threat. Many extraction operations are active in this region, and telecommunications coverage and security presence are poor, so this makes them easy targets for ambush attacks or abduction of company employees, resulting in lucrative opportunities for armed groups and creating a volatile environment for businesses. Therefore, there is a desire from militants to maintain these remote conditions to facilitate their illegal operations. Resistance against the development of the area to improve telecommunications for locals can be viewed as a threat and a genuine risk for telecom companies looking to work in this area.
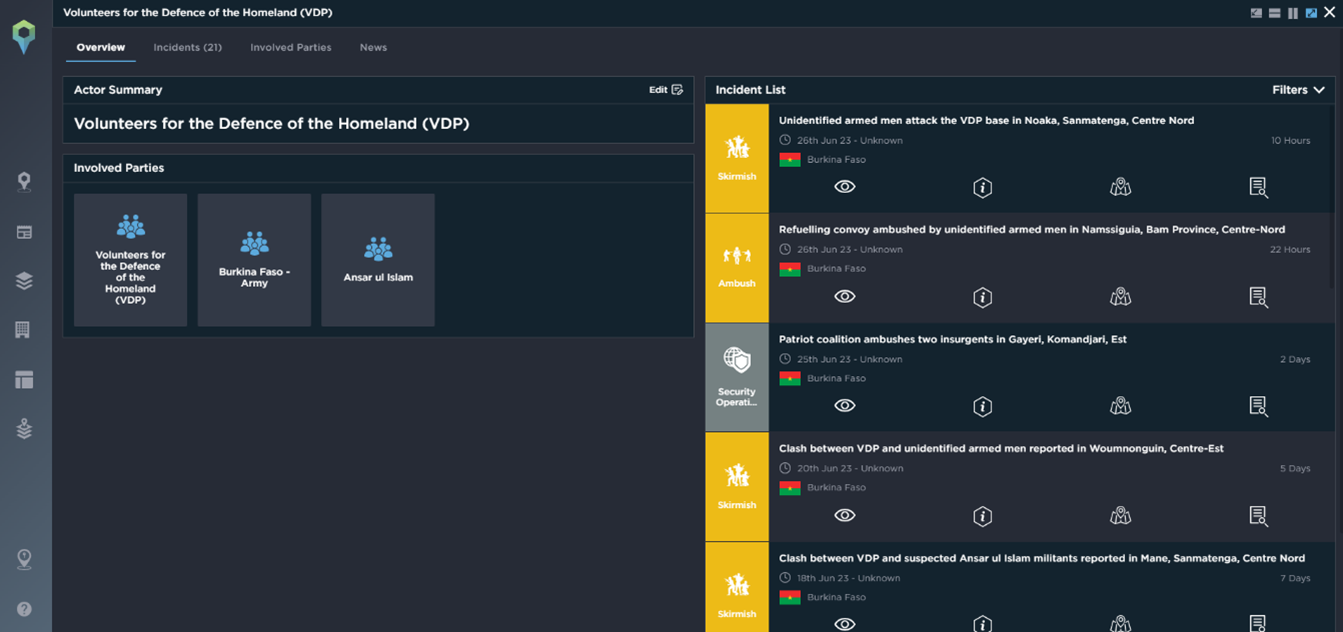
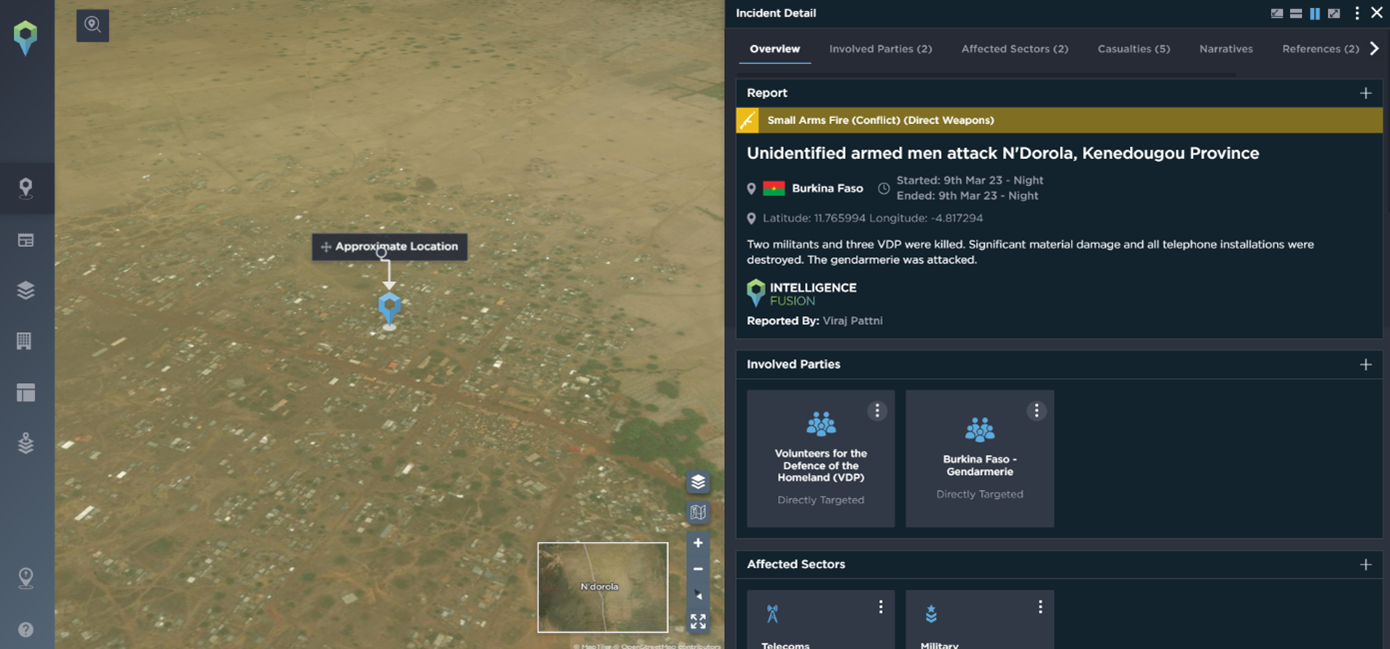
In March this year, armed groups attacked the gendarmerie brigade of Tougouri in the province of Namentenga (Centre-Nord). Two militants and three VDPs were killed. Significant material damage and all telephone installations were destroyed. Two actors were involved in the attack – Volunteers for the Defence of the Homeland (VDP) and Burkina Faso – Gendarmerie.
Actor profiles on the Intelligence Fusion platform allow clients to take a deeper dive into the analysis seeing linked incidents, other involved parties, real-time news updates and more. This aids further analysis and provides added context that helps to mitigate risk.
Natural Hazards
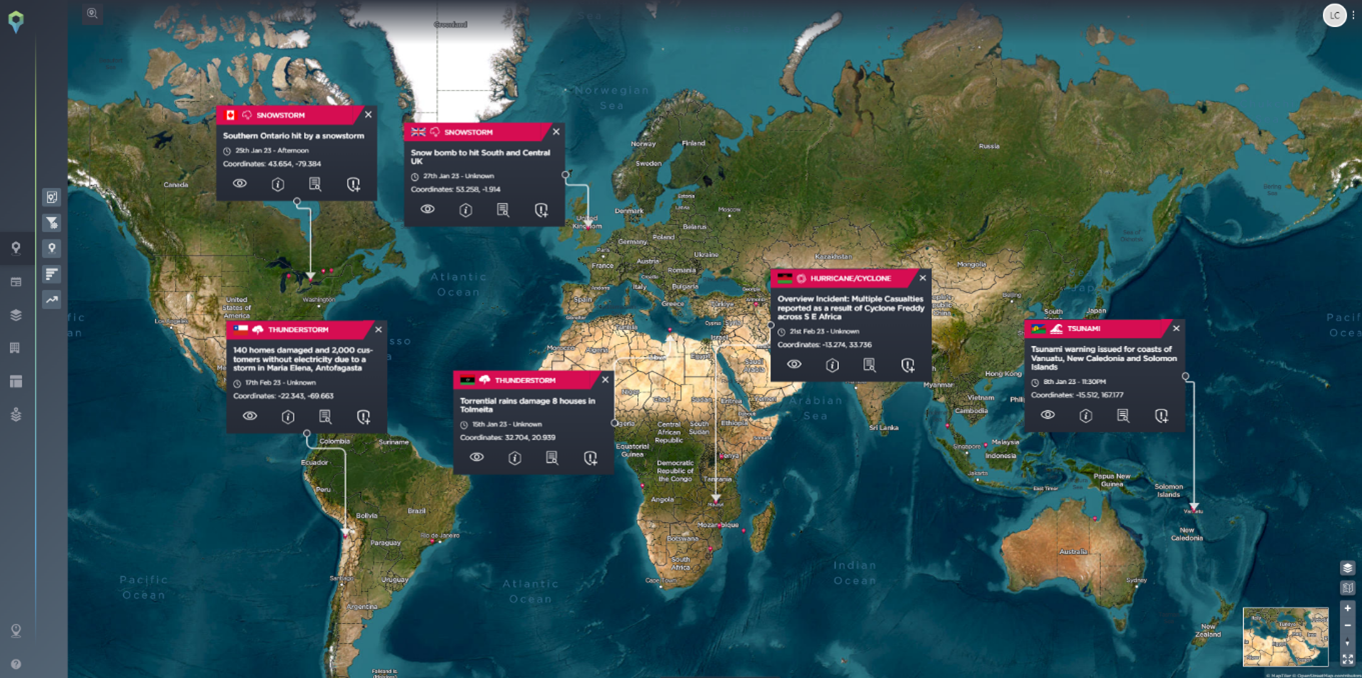
Infrastructure is exposed to environmental factors such as extreme temperatures, humidity, dust, or corrosive conditions. These factors can cause equipment failures, leading to service disruptions and compromising the physical security of the infrastructure. Increasingly severe weather conditions across the globe are escalating threats for all industries.
[Image Source: Intelligence Fusion]
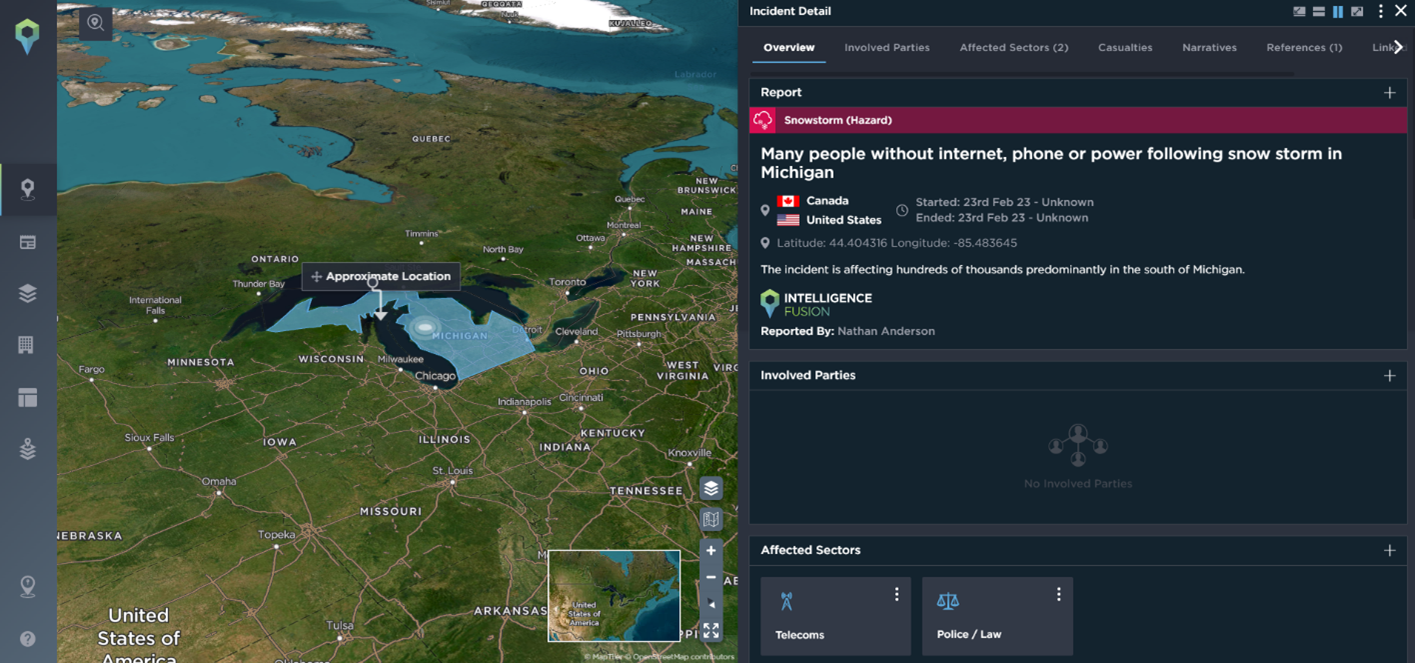
At the start of the year, a major snowstorm caused disruption across networks; many people were left without internet, phone or power in Michigan. Advanced warning of natural hazards affecting clients’ assets allows alerts to be sent ahead of time. In this instance, telecom companies could have warned their customers and provided better customer service had they been aware of the disruption before it occurred. Disaster prevention strategies could have been triggered, and disruption would have been kept to a minimum.
With our new weather feed, we report approx. 30,000 incidents per month and have one of the most comprehensive natural hazard datasets on the market. This, coupled with our analyst’s intelligence, allows us to ensure no major natural hazard is missed and additional context can be added to provide further insights for customers.
[Image Source: Intelligence Fusion]
Supply Chain Vulnerabilities
The telecom industry relies on a complex global supply chain to procure equipment and components. Supply chain vulnerabilities, such as counterfeit or tampered equipment, can compromise the security and reliability of telecom networks.
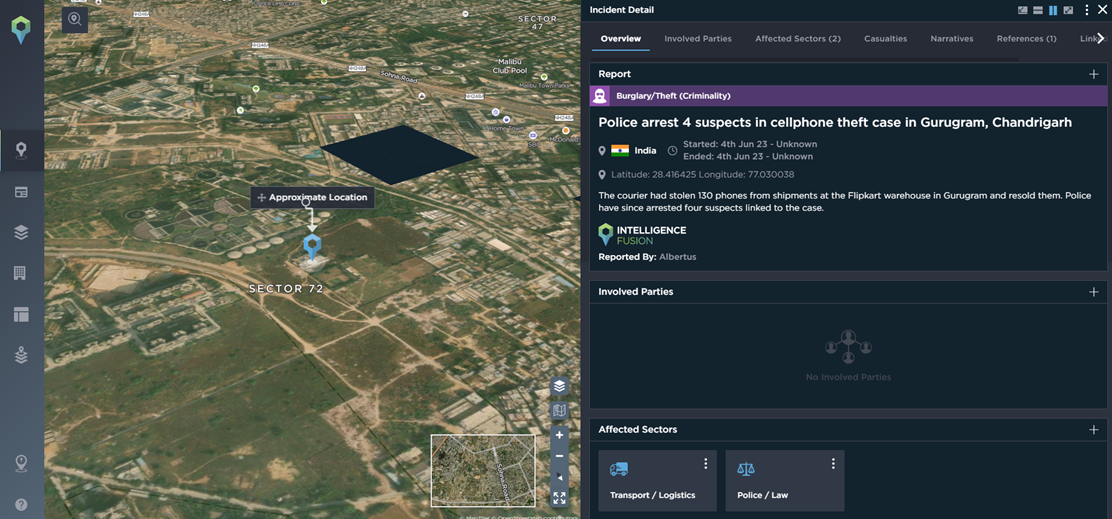
An example is from earlier this year when over 12,000 counterfeit mobile phones were seized in Madrid. This can cause major reputational damage for companies if counterfeit products get to market. Another example of supply chain disruption was in India in June this year when 130 mobile phones from shipments at the Flipkart warehouse in Gurugram were stolen and resold. Police arrested four suspects linked to the case.
Being alerted to this activity can allow customers to keep track of competitors and other stakeholders, as well as gain insight into transport routes that are at higher risk and more susceptible to sabotage or theft. Mapping supply chains and assets can give our customers a high-level overview of incidents which have varying impact ratings and can minimize threats to their business before a major issue occurs.
[Image Source: Intelligence Fusion]