How to tailor data with a threat intelligence API?
A database of irrelevant information is useless, but how do you create a feed of data that aligns with your business priorities?
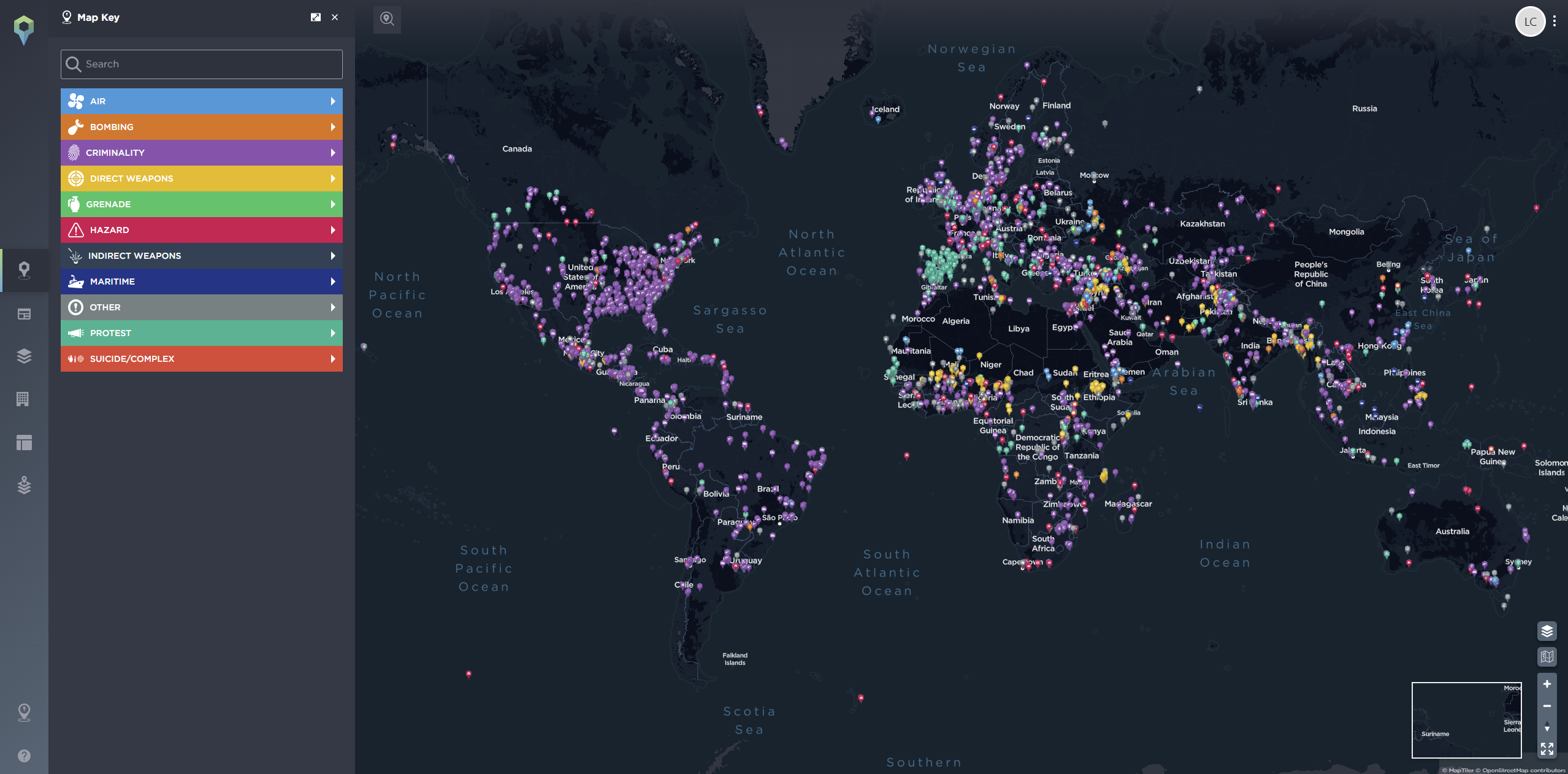
If you already have a platform for visualising threat data, you can supplement it with additional data to create a list of relevant information important to your business and customers, helping to better protect businesses, people, and assets.
Planning and Direction
Firstly, understanding your business’s priorities is essential. It may seem obvious, but many organisations struggle to articulate their goals and aims. This is important whether you use a team of in-house analysts to gather information, API solutions, or a mixture of the two.
It is especially important when using any third party to collect data for your business to clearly communicate your goals and business priorities in order to gain quality data that meets your criteria.
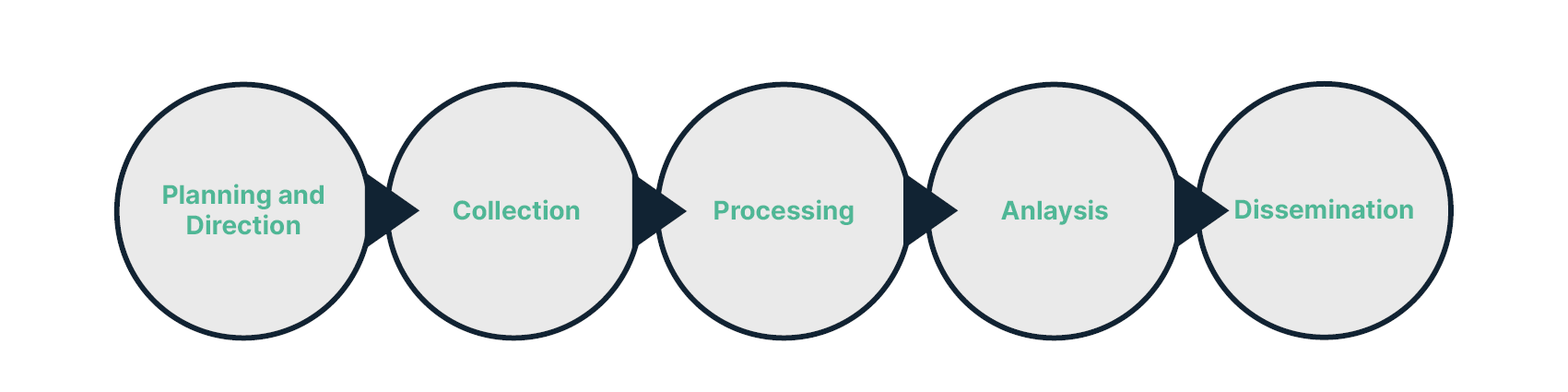
At Intelligence Fusion, our work is based on military principles used in intelligence collection. We use the intelligence cycle as the basis for our business to ensure we remain a customer-focused organisation.
Stage one of the intelligence cycle is planning and direction. This stage is the most critical when developing a feed of tailored data. Ask yourself:
- What are the biggest threats to your organisation?
- What do your customers care most about?
- What regions are most critical for your organisation’s operation?
- Are there any particular actors that could impact your organisation?
- What are your business priorities?
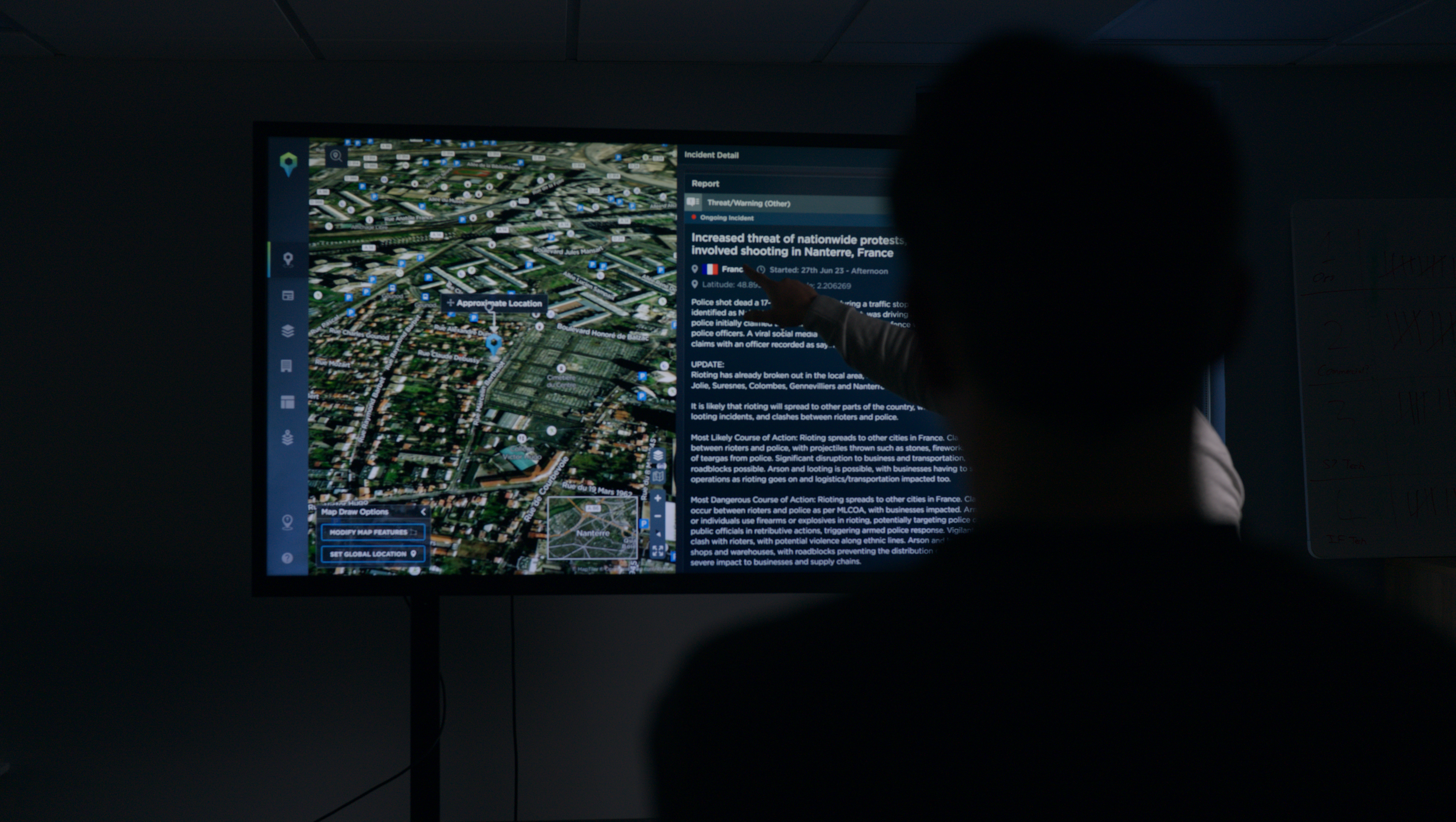
When onboarding a new API customer at Intelligence Fusion, we spend time at the start of the relationship to understand all these questions and more so that our analysts can see the world through your eyes. The more detailed picture we can gain about your organisation, the better the data collection will be. All this information is then added to an ICP or Intelligence Collection Plan – a working document that will change as your business changes. It provides transparency and clarity between your team and our analysts.
The Intelligence Cycle
Collection
The second stage of the intelligence cycle is data collection. Once you have established a solid plan and clear direction, the collection phase can begin. In theory, this should be quite straightforward for businesses to implement. However, it is important to select an API solution from a company that is committed to creating solutions based on your needs rather than generic threat intelligence collection for a wider audience.
At Intelligence Fusion, we have a team of over 20 intelligence analysts who monitor the threat landscape 24/7. They research and verify every incident, bringing diverse skill sets and intelligence backgrounds, from the military to air traffic control, maritime, banking, and more. Within the team, multiple languages are spoken, adding greater value for our clients.
- We report over 20,000 fully verified incidents each month.
- There are over 1,200,000 historical data points on our platform.
- Our AI-assisted news feed crawls more than 1 million news articles every month – that’s 23 articles per minute.
- We produce a minimum of 6 pieces of operations-led content per month.
In addition, every API licence we sell comes with a commercial licence as standard. This means you can resell your solution, creating a new revenue stream and gaining a full return on your investment. In fact, you can save up to 95% by purchasing our threat intelligence API instead of creating your own solution from scratch.
Processing
The third stage is processing. If you select a professional, trustworthy API solution, all the hard work will be done for you.
At this stage, our analysts collate, evaluate, analyse, and interpret the data, ensuring depth and accuracy before reporting it on our data feed. Information is categorised and grouped into themes, incidents are linked and associated with specific actors, and the credibility of the source is graded, along with the impact and potential consequences. Information is compared with other sources, accurately geolocated, and commentary is added. Trends and patterns can then be realised as new incidents are integrated with historical data, allowing analysts to gain a deeper understanding of the situation. Common sense, knowledge, and experience are core parts of this process; hence, open-source intelligence training and a practical background in intelligence or similar disciplines are vital.
Processing and storing data in a format that is usable and easily accessible can be challenging as every system is built differently. We use our own in-house technical team, meaning our clients have 24-hour support if needed, and we also maintain our API internally. This provides:
- A tailored and efficient approach
- Improved cybersecurity
- Alignment with your organisation’s specific needs and strategic goals
Analysis
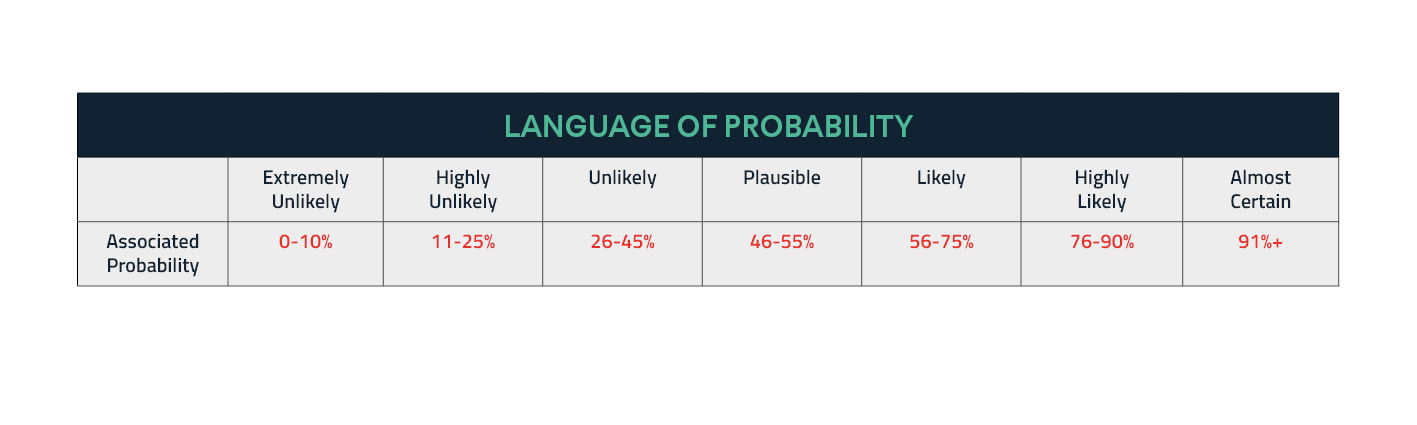
The fourth stage is analysis, which can be challenging for individual companies as it takes years of experience to accurately assess the most likely and most dangerous courses of action in various situations. Analysts at Intelligence Fusion use the language of probability to grade the likelihood of an event occurring. This military terminology ensures intentional and accurate descriptions are used to explain situations and the risks to businesses, avoiding any ambiguity. The analysis stage also turns raw data into useful information, enabling businesses to make more confident decisions by understanding the implications of the incidents presented to them.
Our operations team regularly writes free intelligence reports, covering a range of topics that many of our clients use in briefings and reports as references. We also offer custom reports on topics that matter most to your business; these can be one-off requests if you need to leverage our analysts’ knowledge for a particular situation. Additionally, you can have a one-to-one relationship with our analysts, allowing you to ask questions and gain a deeper understanding of the impact on your business.
The language of probability framework
Dissemination
The final stage is dissemination, which refers to the quality of delivery, including speed, consistency, ease of use, and clarity. For API customers, we ensure the data is always provided in a consistent, standardised format, offering maximum granularity. Our clients can use as much or as little data as they like to build out their database. With over 10 years of development experience, our growing team of technical experts ensures a seamless integration, allowing you to have your new data feed live within a matter of days.
It is then up to you to ingest our data and present it in the best way for your team and/or your customers. The data provided by Intelligence Fusion can include historical data points for research and planning, real-time data about ongoing events, or emerging threats that have not yet occurred but are deemed highly likely to happen and pose a threat to your business.